
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Challenges in Cross Border Data Flows and Data Loc...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-19-2022
2:23 PM
(Jana Subramanian is APJ Principal Cybersecurity Advisor for Cloud Security and Fellow of Information Privacy (FIP) awarded by International Association of Privacy Professional (IAPP). Jana supports strategic customer engagements on cybersecurity, data privacy, multi-cloud security architecture, contractual assurance, audit, and compliance domains.)
Introduction
Recently, major cloud service providers in a shared initiative have come up with the “Trusted Cloud Principles”. This is a commitment from cloud service providers to customers to ensure that privacy and security of customer’s data is maintained across borders. One of the principles which is paramount in “Trusted Cloud Principles” is that governments should support the cross-border flow of data as an engine of innovation, efficiency, and security, and avoid data residency requirements.
We live in a globalized digital world where borders have blurred. It is a common knowledge that enabling cross-border data flow stimulates economic growth and electronic commerce. Around the world, Governments must regulate, ensure safeguards to protect privacy of the individuals and personal data. However, we notice increasingly inconsistent and conflicting laws exist across borders, where the data flow is restricted and an additional requirement to store data in local servers. In this blog, we analyze the nuances of emerging regulations (such as India, China) on cross-border data flow, data localization requirements and a possible approach that organization take to fulfil data localizations obligations.
Data Sovereignty, Data Residency and Data Localization
Before, we elaborate on this subject, let us define differences between data residency, data sovereignty and data localizations in the diagram below. Often, these definitions are used interchangeably, blurring the meaning.
Personal data localization remains to be one of the most challenging problems in cloud computing. In SaaS model, businesses operate globally. It is hard to create local servers and storage to keep such a sensitive data for processing. Such an arrangement creates barrier to free flow of data across the borders. The impact is diminished ability to realize best values of that data, thereby affecting the customer experience.
Restrictions on Cross-Border Data Transfer
India
Currently, Section 43A in The Information Technology Act, 2000 explicitly deals with data protection on handling sensitive personal data. However, until now India does not have a national regulatory authority for protection of personal data. India is the powerhouse of IT services and business process outsourcing (BPO) and the IT industry accounted for 8% of India’s GDP in 2020. Cognizant of the growing need for strong personal data protection, the Ministry of Electronics and Information Technology tabled ‘Personal Data Protection Bill 2019 (PDPB 2019)’ in the parliament. After a numerous deliberation in the last two years, the Joint Parliamentary Committee submitted its long-awaited report to the Indian Parliament in December 2021. The salient aspect of the PDPB 2019 is that it has been renamed as “Data Protection Bill” to cover both personal and non-personal data. A single administration and regulatory body are required to regulate both non-personal data and personal data.
In PDPB 2019 defines a term called ‘data fiduciary’. It refers to any person, including the state, a company, any juristic entity, or any individual who alone or in conjunction with others determines the purpose and means of processing personal data. It is equivalent as ‘Data Controller’ definition in GDPR. The term “Data Processor” has similar meaning as any person, including the state, a company, any juristic entity or any individual, who processes personal data on behalf of a data fiduciary.
There have been numerous criticisms on severely restrictive rules applied to “sensitive” and “critical” personal data across borders and burdensome breach notification obligations. The PDPB 2019 requires a copy of the sensitive personal data to be stored in servers located in India. Exception to this requirement is, when explicit consent of the data principal and subject to standard contractual clauses or Data Protection or Central Government in consultation with DPA is available. It must be noted that “financial data” is considered within the scope of sensitive personal data and cloud service providers must store a copy of such data in servers and storage maintained in India.
The central government may classify certain categories of data as “critical” data. Data in this category must be stored and processed in India. Transfer of such data outside of India is prohibited. Interestingly, financial data and passwords were considered as “Sensitive Personal Data” earlier, but “password” has been removed from the list in 2019 draft version.
Recently, the Data Security Council of India (‘DSCI’) published a whitepaper addressing key considerations for public sector enterprises in migrating to cloud-based solutions which can be downloaded from the link. The whitepaper provides clarity to decision-makers through cloud service adoption and outlines privacy, data residency, security, and contractual considerations in alignment with the Personal Data Protection Bill, 2019.
You can refer to the link on some of the proposed changes to the Data Protection Bill in the link.
China
China’s Data Privacy Laws and Framework is currently in a state of flux. At the outset, the enactments appear to be quite involved. China has enacted comprehensive Personal Information Privacy Law (PIPL). The PIPL and GDPR share some similarities but contrast in many aspects. It is a law effective 1st November 2021. There is also “Data Security Law” enacted by Standing Committee of China’s National People’s Congress (“NPC”) which has come into effect since September 1, 2021. Earlier, China had enacted “Cybersecurity Law (CSL) which came into effect on June 1, 2017.
The CCSL apply to Critical Information Infrastructure Operators (“CIIO”) to store select data within China and allows Chinese authorities to conduct spot-checks on a company’s network operations. Besides, China has formulated sector specific laws and regulations regarding the protection of personal information of customers in highly regulated industries and sectors.
With a labyrinth of laws, regulations, and framework, the requirement on data localization and cross-border data transfer is dispersed across a multitude of regulations. While the definition of “personal information” is broadly consistent with other national standards, the definition of “important data” is ambiguous and Data Security Law has made this a responsibility of the central government to publish a national level catalogue of “important data” and calls for regional and sectoral regulators to issue more detailed catalogues to further identify the scope of “important data” in their regions and sectors. The above data type mentioned pertain to DSL and PIPL only.
There are other type pf data that are subject to data localization requirements in China other than personal information and important data. It should be noted that Chinese authorities may require data localization related to state secrets, government sensitive data and specific industries such as automobile data, Telecom data, Petroleum data and other Industrial data.
Similarly, an important consideration to determine data localization is to determine if an industry comes under Critical Information Infrastructure (CII). The broad definition of CII as an infrastructure that might seriously endanger national or public interests if damaged. However, there is no guidance or criteria for determining what can be considered as CII. On September 1, 2021, the Regulations on Security and Protection of Critical Information Infrastructure took effect, and the regulation provided some factors of consideration on how the authorities will determine a system or facility constitutes CII.
You can refer to IAPP blog “The future of data localization and cross-border transfer in China: a unified framework or a patchw.... It sheds more light on the challenges with various regulations in China. There is another interesting IAPP blog “Analyzing China’s PIPL and how it compares to the EU’s GDPR” which provides nuances on the differences between GDPR and PIPL.
Approach to Data Localization:
The “personal information processing entity” (data controller) is advised to understand the categories of data, localization and cross-border requirements and understanding the variety of data and security regulations & frameworks in China (equivalent of “Data Controller” in GDPR).
Further, as per Article 59, persons entrusted to process personal information (equivalent of “data processor” under the GDPR) are also required to “understand” the requirements under the PIPL and are obligated to assist the “personal information processing entity” (data controllers) to comply with the PIPL.
Based on the above premise, customers have few choices in determining their instance strategy for determining data localization while considering the regulatory landscape in China. The following sections provides broad perspectives on the approaches. It is entirely up to customers to decide their strategy based on the data localization requirement relevant to their business.
Global Instance outside of China for all entities
It is possible to consider global instance strategy and allow global group of companies including entities in China to use it so long as data processing does not exceed certain volume limit and only when it meets all the regulatory requirement related to data localization and cross-border data transfer. It is expected that Chinese authorities to release more and more implementation regulations for PIPL and DSL and there may be instances where non-CIIOs are subject to cross-border data transfer requirements too (as provided for under the DSL)
Global Instance for Group Companies and Local Instance for China Entity Only
A hybrid approach can be that a local instance may be kept for Chinese entities only, as the data may be considered as an “important data” or operating in a highly regulated industry where data localization may be mandated by law. This will require a global instance for group company entities excluding China and a local instance for china entities.
Local Instance in China
If most group entities are in China (where majority of companies and users reside in China and small group of companies outside of China), a local instance in China may be considered with security safeguards and controls. The global group can access instance in China subject to contractual assurances, security safeguards and technical organizational measures.
In summary, it should be clearly understood that an approach for data localization and decision on where the customer wants to host their data must be determined based on their business context and regulatory landscape, type of data, data localization requirements, category of the industry, technical and performance constraints among other factors. In general, the cloud service providers will not be able to determine or advise on regulatory matters and customers must take independent legal advice, given the complicated regulatory landscape in China.
SAP Data Protection and Privacy Solutions
The following section, we look at the tools available for Data Protection and Privacy. These tools would greatly help DPO with compliance & regulations. The Article 5 of the General Data Protection Regulation (GDPR) sets forth the underlying data protection principles. This has become a foundational principle for many of the regional data protection regulations including Personal Data Protection Bill 2019 (India) and Personal Information Protection Law (China). It is imperative for data controllers to deploy solutions using tools that comply with these foundational principles.
SAP provides contractual assurance on personal data processing via SAP personal data processing agreement . It can be found in SAP Trust Center. SAP product and solutions are designed with privacy by default and includes privacy design. It includes capabilities to define privacy. Data Controllers can configure the systems to ensure compliance with core data protection and privacy principles such as transparency, purpose limitation, storage limitation and data minimization. In the sections below, we will abstractly explore tools available to apply data protection and privacy principles.
SAP Data Custodian
Given the data localization requirement and increasing use of public cloud services by our customers, Data Protection Officers (DPO) require tools that provide transparency and control of their data. SAP Data Custodian offers a SaaS based data transparency and control capability, where customer can have visibility on where their data is located, accessed. It generates compliance report on demand. The SAP Data Custodian provides additional functionality such as Regulatory Policy Templates (such as GDPR, PCI-DSS, CCSL, CSRF), Access Control, data transparency and control. A summary of features of SAP Data Custodian is as follows and more information can be found at the link.
UI Masking and Logging:
This tool helps to implement the principle of data minimization, data transparency, accountability with an ability conceal specific data unless it is required for tasks to be performed by authorized users only, thereby, rendering sensitive data unavailable for data abuse. The masking is applied at the UI layer, not at the database layer providing enhanced performance with masking. This works on wide range of UI technologies which include UI5 Fiori, S/4HANA, SAP GUI, WebDynpro ABAP.
UI logging helps to keep data accessible and with an ability to create broad, deep log of data access. With built-in log analyzer, UI logging function ensure compliant behavior, identify anomalies early in time and baseline for deciding actions. The UI logging provides near real-time notifications when certain data is accessed, through SAP notification framework and supports near real-time through integration with Enterprise Threat Detection.
Conclusion:
The implication of non-compliance to regulatory requirements across geographies can be far reaching to the business. It includes and not limited to, damage to reputation and hefty penalties. Data protection and privacy are evolving as a separate specialization, given the huge impact on businesses as organizations move into cloud services in an ever growing and complex regulatory landscape. Data privacy becomes even more complex with adoption of technologies such as AI and Machine Learning for automatic processing, and automatic profiling. There is a growing sense among the community that a more unified approach must be adopted by governments and hence, the initiative by CSPs on “Trusted Cloud Principles” is a step in right direction.
(Disclaimer: The perspectives or opinions expressed in this blog are for information purposes only and should not be construed as a legal advice. The content in this blog does not constitute any representation, or any commitment or legal obligation on the part of SAP)
Introduction
Recently, major cloud service providers in a shared initiative have come up with the “Trusted Cloud Principles”. This is a commitment from cloud service providers to customers to ensure that privacy and security of customer’s data is maintained across borders. One of the principles which is paramount in “Trusted Cloud Principles” is that governments should support the cross-border flow of data as an engine of innovation, efficiency, and security, and avoid data residency requirements.
We live in a globalized digital world where borders have blurred. It is a common knowledge that enabling cross-border data flow stimulates economic growth and electronic commerce. Around the world, Governments must regulate, ensure safeguards to protect privacy of the individuals and personal data. However, we notice increasingly inconsistent and conflicting laws exist across borders, where the data flow is restricted and an additional requirement to store data in local servers. In this blog, we analyze the nuances of emerging regulations (such as India, China) on cross-border data flow, data localization requirements and a possible approach that organization take to fulfil data localizations obligations.
Data Sovereignty, Data Residency and Data Localization
Before, we elaborate on this subject, let us define differences between data residency, data sovereignty and data localizations in the diagram below. Often, these definitions are used interchangeably, blurring the meaning.

Figure 1: Data Residency, Data Sovereignty and Data Localization
Personal data localization remains to be one of the most challenging problems in cloud computing. In SaaS model, businesses operate globally. It is hard to create local servers and storage to keep such a sensitive data for processing. Such an arrangement creates barrier to free flow of data across the borders. The impact is diminished ability to realize best values of that data, thereby affecting the customer experience.
Restrictions on Cross-Border Data Transfer
India
Currently, Section 43A in The Information Technology Act, 2000 explicitly deals with data protection on handling sensitive personal data. However, until now India does not have a national regulatory authority for protection of personal data. India is the powerhouse of IT services and business process outsourcing (BPO) and the IT industry accounted for 8% of India’s GDP in 2020. Cognizant of the growing need for strong personal data protection, the Ministry of Electronics and Information Technology tabled ‘Personal Data Protection Bill 2019 (PDPB 2019)’ in the parliament. After a numerous deliberation in the last two years, the Joint Parliamentary Committee submitted its long-awaited report to the Indian Parliament in December 2021. The salient aspect of the PDPB 2019 is that it has been renamed as “Data Protection Bill” to cover both personal and non-personal data. A single administration and regulatory body are required to regulate both non-personal data and personal data.
In PDPB 2019 defines a term called ‘data fiduciary’. It refers to any person, including the state, a company, any juristic entity, or any individual who alone or in conjunction with others determines the purpose and means of processing personal data. It is equivalent as ‘Data Controller’ definition in GDPR. The term “Data Processor” has similar meaning as any person, including the state, a company, any juristic entity or any individual, who processes personal data on behalf of a data fiduciary.
There have been numerous criticisms on severely restrictive rules applied to “sensitive” and “critical” personal data across borders and burdensome breach notification obligations. The PDPB 2019 requires a copy of the sensitive personal data to be stored in servers located in India. Exception to this requirement is, when explicit consent of the data principal and subject to standard contractual clauses or Data Protection or Central Government in consultation with DPA is available. It must be noted that “financial data” is considered within the scope of sensitive personal data and cloud service providers must store a copy of such data in servers and storage maintained in India.
The central government may classify certain categories of data as “critical” data. Data in this category must be stored and processed in India. Transfer of such data outside of India is prohibited. Interestingly, financial data and passwords were considered as “Sensitive Personal Data” earlier, but “password” has been removed from the list in 2019 draft version.

Figure 2: Data Localization Requirements in India
Recently, the Data Security Council of India (‘DSCI’) published a whitepaper addressing key considerations for public sector enterprises in migrating to cloud-based solutions which can be downloaded from the link. The whitepaper provides clarity to decision-makers through cloud service adoption and outlines privacy, data residency, security, and contractual considerations in alignment with the Personal Data Protection Bill, 2019.
You can refer to the link on some of the proposed changes to the Data Protection Bill in the link.
China
China’s Data Privacy Laws and Framework is currently in a state of flux. At the outset, the enactments appear to be quite involved. China has enacted comprehensive Personal Information Privacy Law (PIPL). The PIPL and GDPR share some similarities but contrast in many aspects. It is a law effective 1st November 2021. There is also “Data Security Law” enacted by Standing Committee of China’s National People’s Congress (“NPC”) which has come into effect since September 1, 2021. Earlier, China had enacted “Cybersecurity Law (CSL) which came into effect on June 1, 2017.
The CCSL apply to Critical Information Infrastructure Operators (“CIIO”) to store select data within China and allows Chinese authorities to conduct spot-checks on a company’s network operations. Besides, China has formulated sector specific laws and regulations regarding the protection of personal information of customers in highly regulated industries and sectors.

Figure 3: Data Privacy Regulations in China
With a labyrinth of laws, regulations, and framework, the requirement on data localization and cross-border data transfer is dispersed across a multitude of regulations. While the definition of “personal information” is broadly consistent with other national standards, the definition of “important data” is ambiguous and Data Security Law has made this a responsibility of the central government to publish a national level catalogue of “important data” and calls for regional and sectoral regulators to issue more detailed catalogues to further identify the scope of “important data” in their regions and sectors. The above data type mentioned pertain to DSL and PIPL only.
There are other type pf data that are subject to data localization requirements in China other than personal information and important data. It should be noted that Chinese authorities may require data localization related to state secrets, government sensitive data and specific industries such as automobile data, Telecom data, Petroleum data and other Industrial data.

Figure 4: Data Localization Requirements in China
Similarly, an important consideration to determine data localization is to determine if an industry comes under Critical Information Infrastructure (CII). The broad definition of CII as an infrastructure that might seriously endanger national or public interests if damaged. However, there is no guidance or criteria for determining what can be considered as CII. On September 1, 2021, the Regulations on Security and Protection of Critical Information Infrastructure took effect, and the regulation provided some factors of consideration on how the authorities will determine a system or facility constitutes CII.
You can refer to IAPP blog “The future of data localization and cross-border transfer in China: a unified framework or a patchw.... It sheds more light on the challenges with various regulations in China. There is another interesting IAPP blog “Analyzing China’s PIPL and how it compares to the EU’s GDPR” which provides nuances on the differences between GDPR and PIPL.
Approach to Data Localization:
The “personal information processing entity” (data controller) is advised to understand the categories of data, localization and cross-border requirements and understanding the variety of data and security regulations & frameworks in China (equivalent of “Data Controller” in GDPR).
Further, as per Article 59, persons entrusted to process personal information (equivalent of “data processor” under the GDPR) are also required to “understand” the requirements under the PIPL and are obligated to assist the “personal information processing entity” (data controllers) to comply with the PIPL.
Based on the above premise, customers have few choices in determining their instance strategy for determining data localization while considering the regulatory landscape in China. The following sections provides broad perspectives on the approaches. It is entirely up to customers to decide their strategy based on the data localization requirement relevant to their business.
Global Instance outside of China for all entities
It is possible to consider global instance strategy and allow global group of companies including entities in China to use it so long as data processing does not exceed certain volume limit and only when it meets all the regulatory requirement related to data localization and cross-border data transfer. It is expected that Chinese authorities to release more and more implementation regulations for PIPL and DSL and there may be instances where non-CIIOs are subject to cross-border data transfer requirements too (as provided for under the DSL)

Figure 5: Global Instance for all Group Companies
Global Instance for Group Companies and Local Instance for China Entity Only
A hybrid approach can be that a local instance may be kept for Chinese entities only, as the data may be considered as an “important data” or operating in a highly regulated industry where data localization may be mandated by law. This will require a global instance for group company entities excluding China and a local instance for china entities.

Figure 6: Hybrid Approach – Global and Local Instance
Local Instance in China
If most group entities are in China (where majority of companies and users reside in China and small group of companies outside of China), a local instance in China may be considered with security safeguards and controls. The global group can access instance in China subject to contractual assurances, security safeguards and technical organizational measures.

Figure 7: Location Instance in China
In summary, it should be clearly understood that an approach for data localization and decision on where the customer wants to host their data must be determined based on their business context and regulatory landscape, type of data, data localization requirements, category of the industry, technical and performance constraints among other factors. In general, the cloud service providers will not be able to determine or advise on regulatory matters and customers must take independent legal advice, given the complicated regulatory landscape in China.
SAP Data Protection and Privacy Solutions
The following section, we look at the tools available for Data Protection and Privacy. These tools would greatly help DPO with compliance & regulations. The Article 5 of the General Data Protection Regulation (GDPR) sets forth the underlying data protection principles. This has become a foundational principle for many of the regional data protection regulations including Personal Data Protection Bill 2019 (India) and Personal Information Protection Law (China). It is imperative for data controllers to deploy solutions using tools that comply with these foundational principles.

Figure 8: Data Privacy Principles
SAP provides contractual assurance on personal data processing via SAP personal data processing agreement . It can be found in SAP Trust Center. SAP product and solutions are designed with privacy by default and includes privacy design. It includes capabilities to define privacy. Data Controllers can configure the systems to ensure compliance with core data protection and privacy principles such as transparency, purpose limitation, storage limitation and data minimization. In the sections below, we will abstractly explore tools available to apply data protection and privacy principles.
SAP Data Custodian
Given the data localization requirement and increasing use of public cloud services by our customers, Data Protection Officers (DPO) require tools that provide transparency and control of their data. SAP Data Custodian offers a SaaS based data transparency and control capability, where customer can have visibility on where their data is located, accessed. It generates compliance report on demand. The SAP Data Custodian provides additional functionality such as Regulatory Policy Templates (such as GDPR, PCI-DSS, CCSL, CSRF), Access Control, data transparency and control. A summary of features of SAP Data Custodian is as follows and more information can be found at the link.

Figure 9: SAP Data Custodian – Security and Compliance
UI Masking and Logging:
This tool helps to implement the principle of data minimization, data transparency, accountability with an ability conceal specific data unless it is required for tasks to be performed by authorized users only, thereby, rendering sensitive data unavailable for data abuse. The masking is applied at the UI layer, not at the database layer providing enhanced performance with masking. This works on wide range of UI technologies which include UI5 Fiori, S/4HANA, SAP GUI, WebDynpro ABAP.
UI logging helps to keep data accessible and with an ability to create broad, deep log of data access. With built-in log analyzer, UI logging function ensure compliant behavior, identify anomalies early in time and baseline for deciding actions. The UI logging provides near real-time notifications when certain data is accessed, through SAP notification framework and supports near real-time through integration with Enterprise Threat Detection.
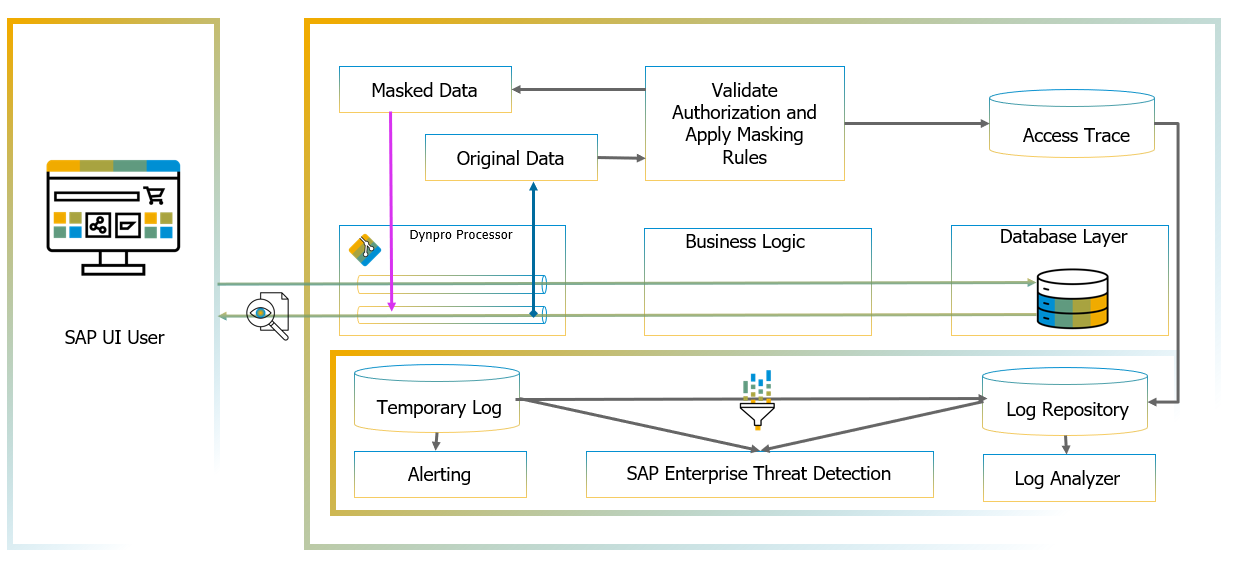
Figure 10: UI Masking and Logging
Conclusion:
The implication of non-compliance to regulatory requirements across geographies can be far reaching to the business. It includes and not limited to, damage to reputation and hefty penalties. Data protection and privacy are evolving as a separate specialization, given the huge impact on businesses as organizations move into cloud services in an ever growing and complex regulatory landscape. Data privacy becomes even more complex with adoption of technologies such as AI and Machine Learning for automatic processing, and automatic profiling. There is a growing sense among the community that a more unified approach must be adopted by governments and hence, the initiative by CSPs on “Trusted Cloud Principles” is a step in right direction.
(Disclaimer: The perspectives or opinions expressed in this blog are for information purposes only and should not be construed as a legal advice. The content in this blog does not constitute any representation, or any commitment or legal obligation on the part of SAP)
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
429 -
Workload Fluctuations
1
Related Content
- Hack2Build on Business AI – Highlighted Use Cases in Technology Blogs by SAP
- SAP Document and Reporting Compliance - 'Colombia' - Contingency Process in Technology Blogs by SAP
- CAP LLM Plugin – Empowering Developers for rapid Gen AI-CAP App Development in Technology Blogs by SAP
- Navigating Compliance and BPM: Challenges & Solutions in Technology Blogs by SAP
- How Data Anonymization in SAP HANA secure Generative AI applications through SAP Datasphere in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 32 | |
| 17 | |
| 15 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |