
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Enhancing Cloud Security: How SAP Business Technol...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
Enterprise companies utilize the SAP Business Technology Platform (SAP BTP) for building cloud-native applications, facilitating business automation, integration and extension, data management and enhancing analytics, among many other capabilities. As we all know in this age of digitalization, cybersecurity becomes paramount as businesses increasingly depend on platforms like SAP BTP to fuel innovation, modernize applications, and drive business growth. However, this dependence also brings significant cybersecurity challenges, especially in light of the prevalent vulnerabilities identified by the Open Web Application Security Project (OWASP). The OWASP Top Ten list is a critical awareness document for developers and web application security professionals, outlining the most significant security risks to web applications and offering essential guidance in the realm of cybersecurity.
This blog aims to explore how SAP BTP's comprehensive array of security controls and services aligns with OWASP's best practice approach to safeguard against critical cyber threats. We'll delve into the specific features of SAP BTP that effectively mitigate OWASP vulnerabilities, offering insights into the platform's multi-layered security approach to securing enterprise applications and operations.
Top 10 OWASP Vulnerabilities
SAP BTP is a crucial element in SAP’s cloud architecture. Central to a multitude of SaaS applications utilized by our customers and within SAP itself, SAP BTP maintains platform capabilities for enhanced security, performance and reliability. In securing SAP BTP’s cloud infrastructure, SAP employs security of cloud foundry environment with HA Proxy, Load Balancers, DNS Security, Proxy services, Network Address Translation, DDoS protection, network-level segregation, security groups, and stringent access controls among many others including security natively available with Hyperscale providers. Beyond these fundamental protections, SAP BTP offers comprehensive security features specifically designed to mitigate OWASP-type vulnerabilities, equipping customers with powerful tools to safeguard their digital landscapes.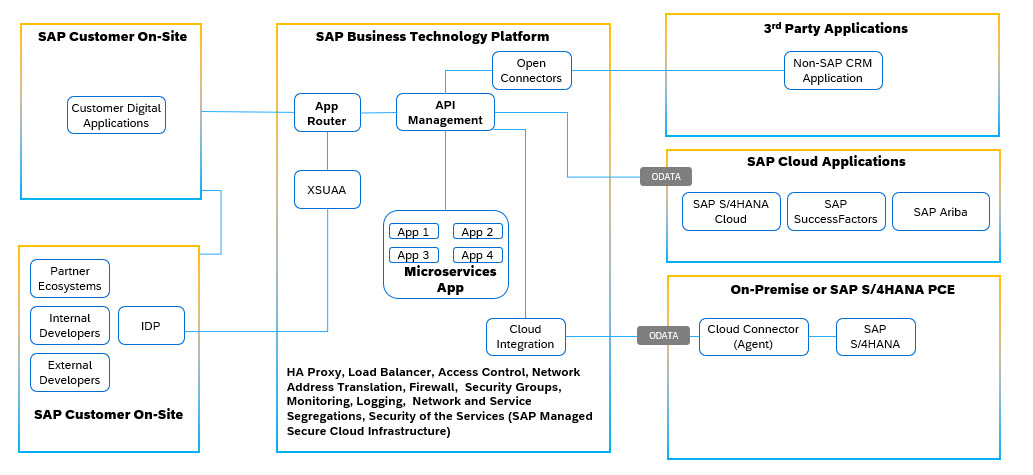
Figure 1: High Level SAP BTP Integration Landscape
Before delving into SAP BTP's security controls, let us summarize the OWASP vulnerabilities last identified as the Top 10.
| Rank | Category | Description |
| A1 | Broken Access Control |
|
| A2 | Cryptographic Failures |
|
| A3 | Injection |
|
| A4 | Insecure Design |
|
| A5 | Security Misconfiguration |
|
| A6 | Vulnerable and Outdated Components |
|
| A7 | Identification and Authentication Failures |
|
| A8 | Software and Data Integrity Failures |
|
| A9 | Security Logging and Monitoring Failures |
|
| A10 | Server-Side Request Forgery (SSRF) |
|
SAP BTP Security Control to address OWASP Vulnerabilities
In the following section, we will focus on the details of how SAP BTP provides capabilities that can be configured to address OWASP vulnerabilities. For clarity, only high-level capabilities are discussed without going into the nitty-gritty of the configuration.
| Rank | Category | SAP BTP Security Capability to address OWASP Vulnerability |
| A1 | Broken Access Control | Within the SAP Business Technology Platform (SAP BTP), several components and protocols play a crucial role. These include the App Router, API Management service, Identity Authentication Service (IAS), Identity Provisioning Service (IPS), OAuth 2.0 protocol, and OpenID Connect protocol. 1. App Router
2. API Management
3. Identity Authentication Service (IAS)
4. Identity Provisioning Service (IPS) and Identity Access Governance
5. OAuth 2.0
6. OpenID Connect
|
The Application Router in SAP BTP, serving as the singular point of entry for applications in the Cloud Foundry environment, performs a multitude of functions. It is responsible for serving static content, authenticating users, rewriting URLs, and forwarding or proxying requests to other microservices with user information propagation. This versatile router is accessible as a library on npmjs.com under @sap/approuter and as a container image on Docker Hub at https://hub.docker.com/r/sapse/approuter.

Figure 2: Secure Flow with AppRouter
| Rank | Category | SAP BTP Security Capability to address OWASP Vulnerability |
| A2 | Cryptographic Failures | 1. Encryption of Data in Transit and at Rest
2. Secure Key Management
3. Secure Cryptographic Algorithms
4. Compliance with Security Standards
5. Secure Communication Protocols
6. Access Control
|
| Rank | Category | SAP BTP Security Capability to address OWASP Vulnerability |
| A3 | Injection | 1. API Management
2. AppRouter
3. Secure Software Development Lifecycle Approach
|
SAP API Management empowers developers to build secure APIs by providing features and policies specifically designed to address common vulnerabilities. This significantly enhances the security of API interactions and offers robust protection against a wide range of cyber threats. Additionally, the platform's ability to enforce stringent security policies, coupled with its seamless integration with other SAP security tools, makes it an indispensable component in strengthening API ecosystems.

Figure 3: API Management Policies
The following diagram offers a high-level view of the secure flow involving AppRouter and API Management.

Figure 4: Secure Flow with API Management
| A4 | Insecure Design | SAP BTP Security Capability to address OWASP Vulnerability |
| A5 | Security Misconfiguration |
|

Figure 5: Secure Authentication and Authorization Flow
The authentication and authorization flow explained well with a diagram in the book “Architecting Solutions with SAP Business Technology Platform” by Serdar Simsekler , Eric Du
| Rank | Category | SAP BTP Security Capability to address OWASP Vulnerability |
| A9 | Security Logging and Monitoring Failures | 1. Comprehensive Logging
2. Real-time Monitoring and Alerting
3. Security Information and Event Management (SIEM) Integration
|

Figure 6: Audit API Retrieval Log
| Rank | Category | Description |
| A10 | Server-Side Request Forgery (SSRF) |
|
Additional References:
Conclusion
SAP Business Technology Platform (SAP BTP) delivers robust security for developers looking to modernize applications, integrate systems, or build extensions. With its comprehensive security measures, SAP BTP offers exceptional protection against a range of OWASP vulnerabilities, a crucial consideration in today’s digital landscape. This level of security is especially vital for developers who need to ensure the safety and integrity of their applications against various web threats.
At the infrastructure layer, SAP has designed and deployed a multi-layered security architecture, utilizing both hyperscale cloud capabilities and a suite of validated third-party and open-source tools and services. For developers, SAP BTP provides a solid security framework encompassing an array of features such as the App Router, API Management, robust authentication, and authorization processes, built in security services for credential store, Secure KMS, thorough audit logging, and efficient malware scanning for documents. These integrated security features effectively mitigate risks and minimize the potential for web application attacks, offering each SAP BTP customer a secure and reliable cloud environment for their business needs.
Disclaimer:
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
- SAP Managed Tags:
- RISE with SAP,
- Cloud Integration,
- SAP Integration Strategy,
- SAP Business Technology Platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
430 -
Workload Fluctuations
1
- Sapphire 2024 user experience and application development sessions in Technology Blogs by SAP
- Deployment of Seamless M4T v2 models on SAP AI Core in Technology Blogs by SAP
- Start page of SAP Signavio Process Insights, discovery edition, the 4 pillars and documentation in Technology Blogs by SAP
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
- Improving Time Management in SAP S/4HANA Cloud: A GenAI Solution in Technology Blogs by SAP
| User | Count |
|---|---|
| 31 | |
| 17 | |
| 15 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |