- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Centralize Authorization Management of SAP Cloud A...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
You are using SAP Cloud ALM – the cloud-based application lifecycle management tool to facilitate and streamline the implementation, operation, and continuous improvement of SAP solutions. In SAP Cloud ALM, SAP Cloud Identity Services - Identity Authentication assumes the role of the identity provider. This means that business users log on to SAP Cloud ALM with the mechanisms and credentials defined in the corresponding Identity Authentication tenant.
If the Identity Authentication service is serving as authenticating identity provider or as a proxy to your corporate identity provider, it is quite obvious that you might also want to centralize the authorization management of SAP Cloud ALM there. This blog presents a method for doing this using SAP Cloud Identity Services - Identity Provisioning – a service that automates identity lifecycle processes and helps you provision identities and their authorizations to various cloud and on-premise business applications.
In this method, the SAP Cloud ALM roles with the respective users are modeled as groups in the Identity Authentication tenant. Communication between these participants is done via the Identity Provisioning service, where they are defined as source and target systems.
Prerequisites
To provision groups from Identity Authentication with their members as roles with users assigned to them in SAP Cloud ALM, the following requirements must be met:
In your Identity Provisioning tenant, your Identity Authentication tenant used as the identity provider for SAP Cloud ALM is defined as a source system. For more information, see https://help.sap.com/docs/identity-provisioning/identity-provisioning/identity-authentication.
In your Identity Provisioning tenant, your SAP BTP XS Advanced UAA running on a SAP BTP Cloud Foundry subaccount is defined as a target system. For more information, see https://help.sap.com/docs/identity-provisioning/identity-provisioning/target-sap-btp-xs-advanced-uaa.... This is the BTP subaccount where SAP Cloud ALM is deployed.
How to do it
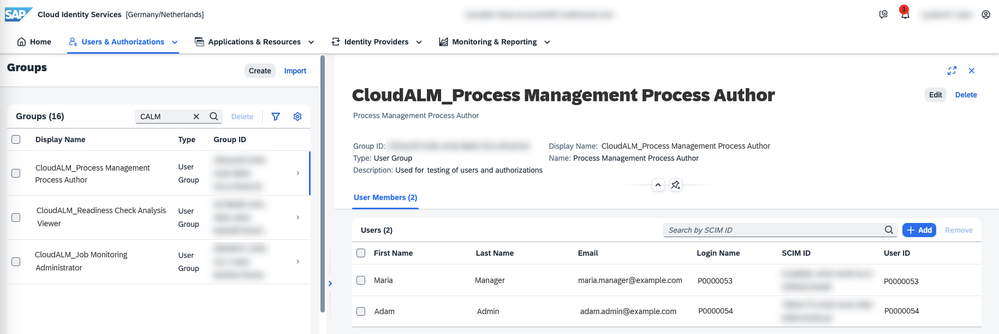
In your Identity Authentication tenant, define the role collections from your BTP subaccount as groups.
It makes sense to use a common prefix for the display name, like CloudALM_– so use CloudALM_ + <Role Collection Name> as the display name of the group. You can use any prefix you like as long as it does not include an & – such a value would not work as a filter value (see below).
There are two reasons for using a common prefix:
When you browse through all groups, you can better distinguish these groups representing the role collections.
Later you create filters ensuring that only groups representing the role collections and their members are provisioned to the BTP subaccount. And a common prefix for the group name makes it much easier to define which groups are to be provisioned.
Add users to these groups according to the authorizations they require for SAP Cloud ALM.
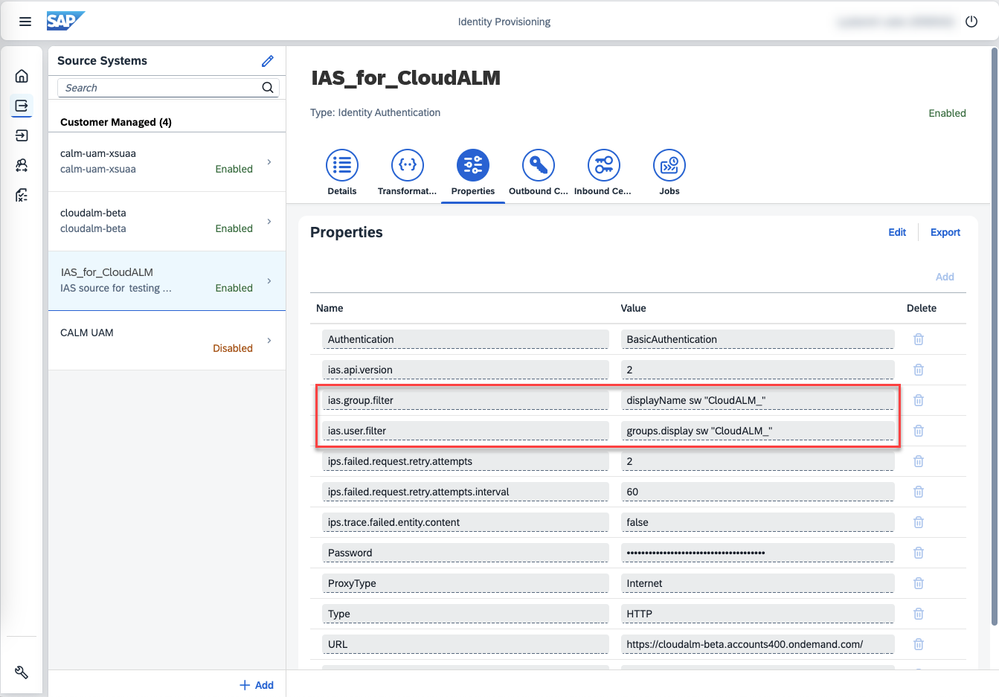
In your Identity Provisioning tenant, navigate to your Identity Authentication source system, tab Transformation, and ensure that the group section of the transformation is enabled – which means that it does not have an entry "ignore": true.
In your Identity Provisioning tenant, navigate to your Identity Authentication source system, tab Properties, and define filters containing your prefix you used above so that only groups relevant for SAP Cloud ALM and their members are provisioned via Identity Provisioning to the BTP subaccount:
ias.user.filter=groups.display sw "CloudALM_"
ias.group.filter=displayName sw "CloudALM_"
Note
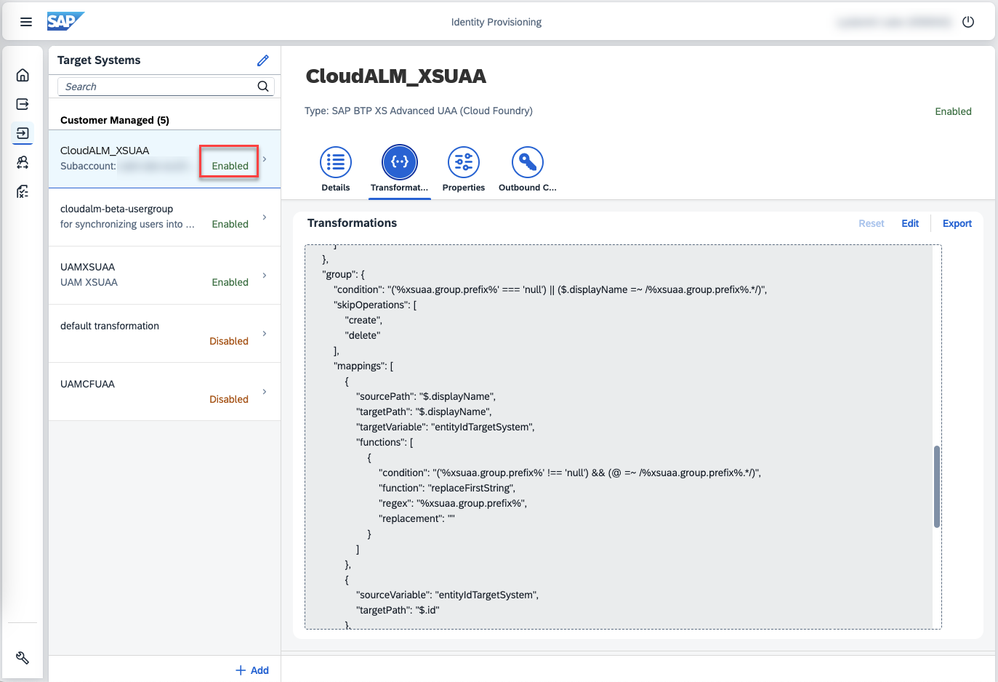
To provision all users from Identity Authentication to the BTP subaccount, you can skip the ias.user.filter.In your Identity Provisioning tenant, navigate to your SAP BTP XS Advanced UAA target system, tab Transformation, and ensure that the group section of the transformation is enabled and it is not ignored.
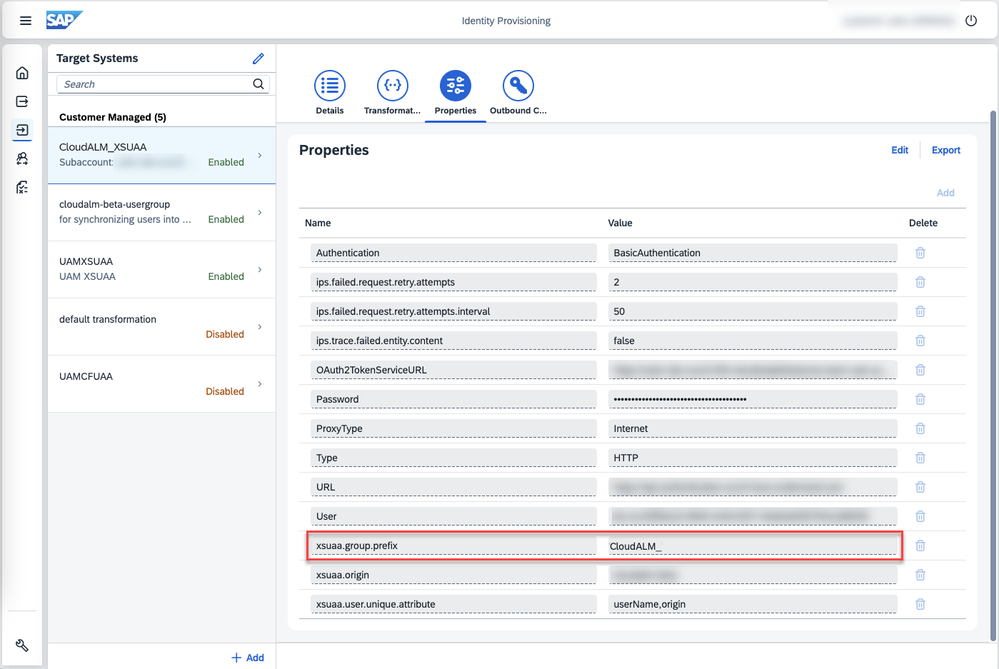
In your Identity Provisioning tenant, navigate to your SAP BTP XS Advanced UAA target system, tab Properties, and define the group prefix you used for the display name. In our example, this is: xsuaa.group.prefix= CloudALM_.
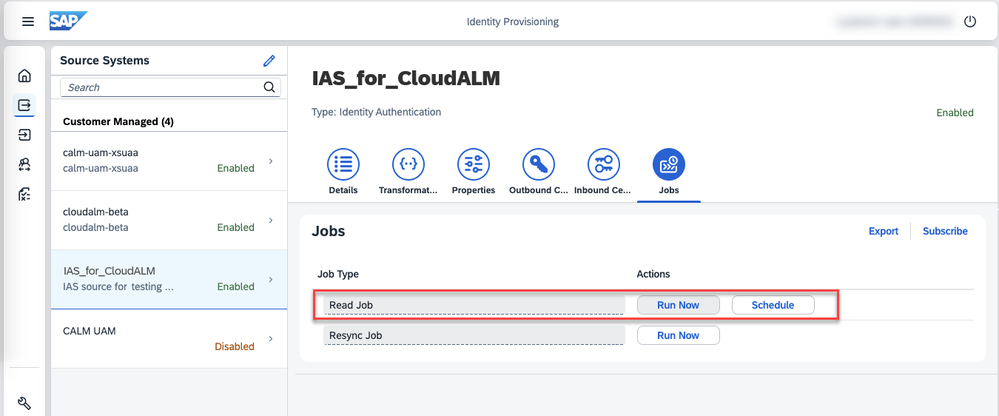
After your source and target systems are configured and enabled, you can now execute the Read Job. To do so, in your Identity Provisioning tenant, navigate to your Identity Authentication source system, tab Jobs.
Usually you want to schedule this job permanently so that later changes to the groups and their members are provisioned to your BTP subaccount and thus also to SAP Cloud ALM.
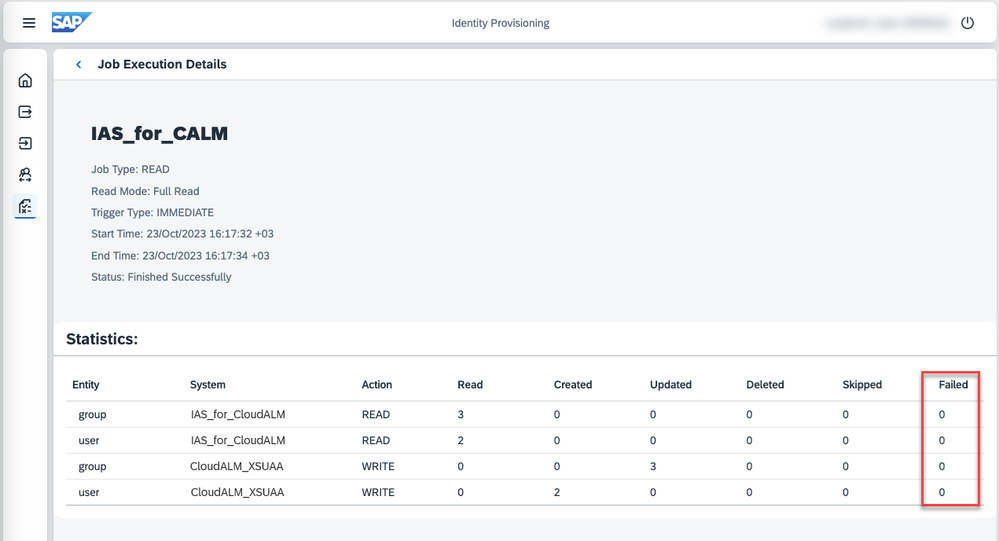
Check the result of the provisioning job. If any errors occur, investigate them and fix them. Some users or groups might not be provisioned, if they are reported as failed. To have them provisioned to SAP BTP XS Advanced UAA with proper authorizations, you have to fix the errors first.
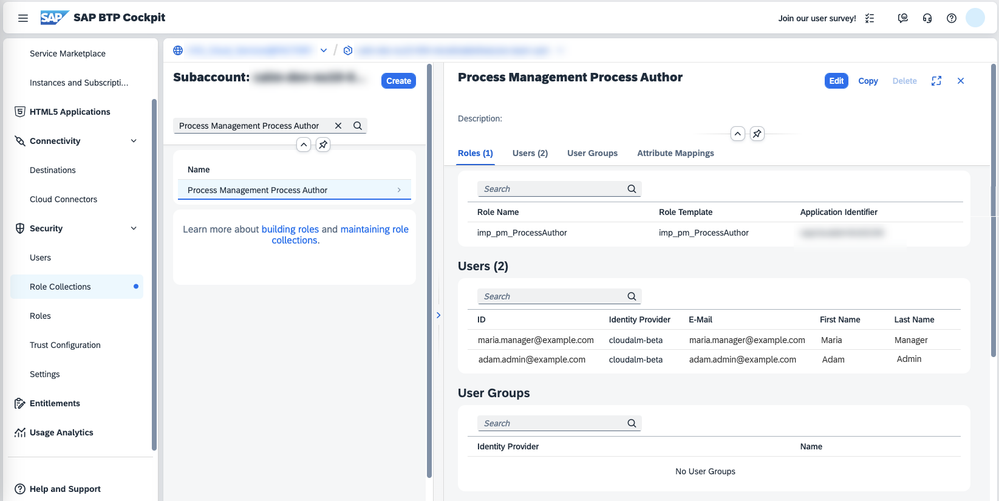
Go to the SAP BTP Cockpit of your BTP subaccount, and select Security -> Role Collections in the navigation bar. The members of the role collection you’ve just created as a group in your Identity Authentication tenant are updated.
That’s it! If you now create groups in your Identity Authentication tenant with your chosen prefix and the name of a role collection, assign users to these groups and wait for the next scheduled provisioning job, then the role collections and their members are updated in your BTP subaccount and SAP Cloud ALM, respectively.
There’s just one thing you should keep in mind: If you delete such a group from your Identity Authentication tenant, the lastly provisioned users in the corresponding role collection in the BTP subaccount are preserved as members of the role collection. So better don't delete such a group at all.
However, if you must, first remove all its members, then let the next job run provision the group to the target system, so that it is updated. Make sure that the role collection has no more members in the BTP subaccount, before you remove the group from Identity Authentication tenant.
- SAP Managed Tags:
- SAP Cloud ALM
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
430 -
Workload Fluctuations
1
- SAP BW/4 - revamp and true to the line 2024 in Technology Blogs by Members
- SAP Cloud ALM and Identity Authentication Service (IAS) in Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- Real time access management with SAP BTP Kyma serverless workloads in Technology Blogs by SAP
| User | Count |
|---|---|
| 30 | |
| 17 | |
| 15 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |