- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by SAP
- GRC Tuesdays: Insights into Cybersecurity Supply C...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Image generated with AI (DALL·E 3)
If cybersecurity risk in the supply chain is the potential for harm or compromise that arises from the cybersecurity risks posed by suppliers, their supply chains, and their products or services, Cybersecurity Supply Chain Risk Management – or C-SCRM for short, is the process of identifying, assessing and mitigating risks in an organization's supply chain for Information and Communications Technology (ICT) products and services that could impact the security and integrity of an organization's products, services and operations.
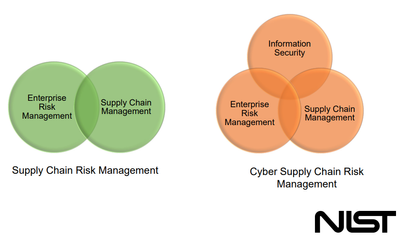
As per the National Institute of Standards and Technology, Cybersecurity Supply Chain Risk Management is at the intersection of information security and supply chain management:
Why should organizations care about C-SCRM?
Long story short: because risk factors continue to increase and are more diverse.
These include external malicious actors of course, but also internal personnel threat, vulnerabilities in product and component development, gaps in physical security, influence from foreign ownership that may not align with the company’s best interest, compliance and legal requirements in relations to counterfeit or non-conforming products, but also evolving sanctions or lists of prohibited suppliers just to name a few.
As a matter of fact, there is a strong realization that root causes for this risk are significant:
Increased dependency on 3rd party vendors, complexity of supply chains & lack of transparency | 98% have been affected by a cybersecurity breach in their supply chain (BCG, 2023) |
Sophistication of attackers and compromised partners | 90% believe they are at risk of a supply chain attack and think vetting software suppliers is a critical activity, but only 33% actually do (NIST, 2021) |
Vulnerable code and implanted backdoors | 633% year on year increase in malicious software supply chain attacks in 2022 (BCG, 2023) |
Rapidly evolving regulatory landscape
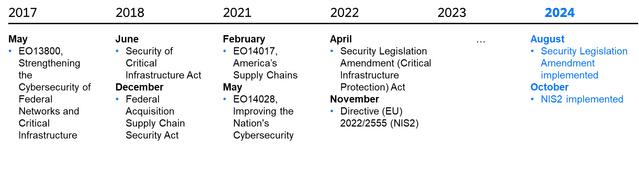
To protect companies and customers many countries and economic regions decided to release guidance to be followed and, in some cases, to give an extra “push”, to issue regulatory requirements. And 2024 will be an eventful year for Cybersecurity Supply Chain Risk Management on that front!
Illustration of select C-SCRM requirements in Australia, Europe and United States
Who should be concerned?
Let’s start answering this question by the industries in scope of Cybersecurity Supply Chain Risk Management recommendations.
And there are many!

| In no particular order, the following industries have been namely mentioned in at least one of the sources listed at the bottom of this blog: Energy, Education, Transport, Financial Services, Health and Medical, Space Technology, Grocery and Food (production, processing and distribution), Water (drinking and waste/sewage), Defence, Communications, Digital Infrastructure (DNS, data centres, storage, Cloud computing), Information and Communications Technology Service, Public Administration, Postal Service, Chemicals, Manufacturing (medical devices, computer and electronic products, electrical equipment, motor vehicles), Research… and more! In essence, every industry where there is an ICT component in the product or service being delivered is in scope. Just think of your wearable device or your connected coffee maker! |
Contrarily to a widespread misconception, Cybersecurity Supply Chain Risk Management isn’t restricted to large companies. Small and medium-sized enterprises are increasingly becoming the target of supply chain attacks.
What steps should you consider?
If your company is in an industry listed just above – or if you just want to ensure the integrity, security, quality and resilience of your supply chain and your products and services, you may decide to implement a Cybersecurity Supply Chain Risk Management approach.
Stakeholder engagement
For it to be successful, representatives or at least 3 stakeholders should be involved in designing the approach:
- Sponsorship by Executive Leadership (ex: CEO, CIO, COO, CFO, CISO, CTO, etc.)
- Decision making by Business Management (ex: Program and Project Management, R&D and Engineering, Procurement, and Quality Assurance, etc.)
- End-users/prescribers’ advice from Operational Management (ex: Architects, Developers, System Owners, Quality Assurance, etc.)
Best practice framework
Once the Governance is defined, then comes the choice of the standard. There are of course different frameworks that can be leveraged, but the 2 major ones have been issued by the National Institute of Standards and Technology (NIST) and by the European Union Agency for Cybersecurity (ENISA):
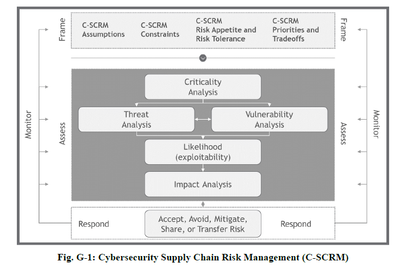
NIST:
ENISA:
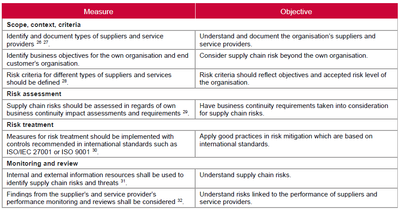 | “Blended” summary: Context and Scope o Identify suppliers & assess criticality o Identify business objectives, risk appetite, and risk tolerance o Document threat sources and vulnerabilities
Assess o Assess supply chain cybersecurity risks o Determine exposure of enterprise operations o Prioritizing risks for mitigation
Respond o Make and document decisions o Implement management, operational, and technical controls o Document contingency plans
Monitor and Review o Monitor risks against appetite and tolerance o Monitor effectiveness of risk responses o Document and track incidents (and resolution) o Screen suppliers o Audit for compliance
|
What benefits can you expect?
Key benefits that organizations implementing a Cybersecurity Supply Chain Risk Management approach can achieve include:
- Reduced likelihood of supply chain compromise
- Operational and enterprise efficiencies
- Greater assurance of quality and reliability of products acquired
- Greater assurance of supplier trustworthiness
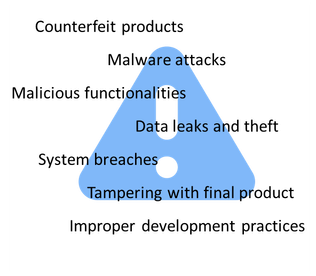
In summary, a sound Cybersecurity Supply Chain Risk Management would help strengthen the supply chain and address risks that can occur at all steps:
Examples of risks in the Design-to-Operate process
What about you, has you company already implemented a Cybersecurity Supply Chain Risk Management approach? If so, what insights would you share with peers looking at doing the same? I look forward to reading your thoughts and comments either on this blog or on Twitter @TFrenehard
And if you are interested in learning more about SAP solutions for Governance, Risk, and Compliance, feel free to fill-in the demo request form!
Additional sources:
Should you want to read more about this topic, I would suggest the following sources:
- Cybersecurity SCRM Fact Sheet, National Institute of Standards and Technology
- Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (SP 800-161r1), National Institute of Standards and Technology
- Case Studies in Cyber Supply Chain Risk Management, Observations from Industry – Summary of Findings..., National Institute of Standards and Technology
- Key Practices in Cyber Supply Chain Risk Management: Observations from Industry (IR 8276), NIST
- Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measur..., European Union
- Good Practices for Supply Chain Cybersecurity, European Union Agency for Cybersecurity
- Identifying Cyber Supply Chain Risks, Australian Signals Directorate
- Management of Cyber Security Supply Chain Risks, Australian National Audit Office
- Supply Chain Cyber Security, New Zealand National Cyber Security Centre
- Strengthening and Enhancing Cyber capabilities by Utilizing Risk Exposure Technology Act, Congress USA
- Federal Acquisition Supply Chain Security Act, Management and Budget Office USA
- Improving the Nation's Cybersecurity, Executive Office of the President USA
- Supply Chain Risk Management Framework, Office of the Secretary of Defense USA
- Supply Chain Cybersecurity: 3 Future Advances, Gartner
- SAP Managed Tags:
- Governance, Risk, Compliance (GRC), and Cybersecurity
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
Business Trends
145 -
Business Trends
15 -
Event Information
35 -
Event Information
9 -
Expert Insights
8 -
Expert Insights
29 -
Life at SAP
48 -
Product Updates
521 -
Product Updates
63 -
Technology Updates
196 -
Technology Updates
10
- SAP Sustainability for Financial Services - Portfolio and Solutions in Financial Management Blogs by SAP
- Event report | Global SAP Financials Forum 2024, April 22-24 (WENFIT) in Financial Management Blogs by SAP
- GRC Tuesdays: Takeaways from the 2024 Internal Controls, Compliance and Risk Management Conference in Financial Management Blogs by SAP
- Navigating Tax Requirements in the Digital Era: Learn How SAP Helps You Revolutionizing Compliance in Financial Management Blogs by SAP
- SAP ECC Conversion to S/4HANA - Focus in CO-PA Costing-Based to Margin Analysis in Financial Management Blogs by SAP
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |