
- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by SAP
- Demystifying Cyber Risk: Empowering SAP Organizati...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
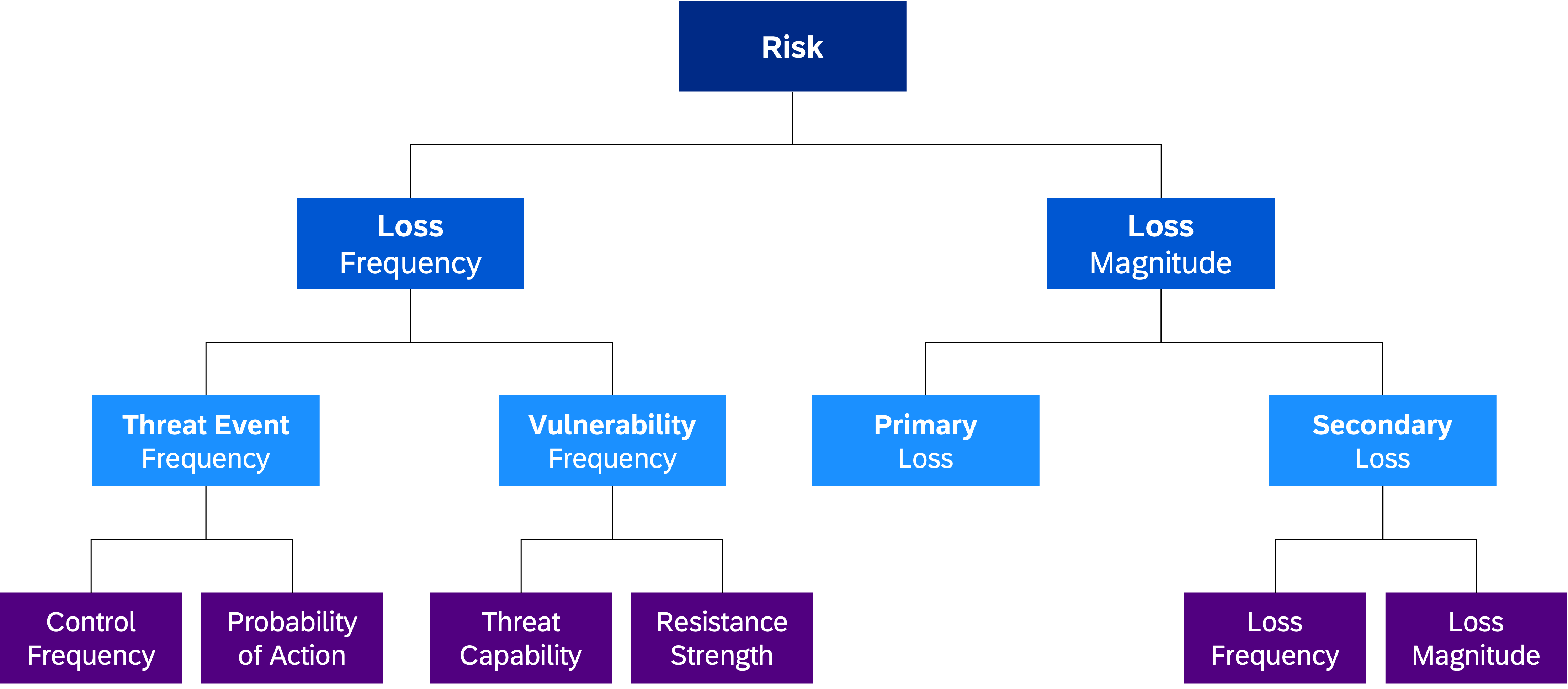
FAIR Methodology (Factor Analysis of Information Risk) for Risk Quantification
In today's digitally driven world, organizations of all sizes and industries face the pervasive threat of cyberattacks.
With businesses relying increasingly on technology and interconnected systems, quantifying cyber risk has emerged as a critical task to increase risk visibility at the board level.
This blog explores how the FAIR (Factor Analysis of Information Risk) methodology helps in quantifying cyber risk, particularly within the SAP realm. It emphasizes the importance of integrating cyber risks into the broader enterprise risk management framework, ensuring that cybersecurity is not treated in isolation but is considered alongside other strategic risks.
By adopting a holistic approach to risk management, organizations can identify and prioritize cybersecurity investments, enhance their incident response capabilities, and safeguard their assets, reputation, and customers.
Quantifying Cyber Risk with the FAIR Model:
The FAIR methodology is a framework for assessing and quantifying information risk in a structured and systematic manner. It provides organizations with a consistent and repeatable approach to evaluating and measuring risk.
It promotes the usage of data-driven methods and probabilistic models to estimate and measure risk in financial terms, providing organizations with a more objective and consistent way to make risk-informed decisions and allocate resources effectively.
“By assigning probabilistic values and monetary figures to these components, organizations can gain a clearer understanding of the financial impact associated with cyber risks.” says Julian Meyrick, VP of Security Strategy Risk & Compliance, IBM.
Integrating Cyber Risks with Enterprise Risk Management:
Quantifying cyber risk with FAIR is essential, but it's just the beginning. Organizations must integrate cyber risks into their broader enterprise risk management (ERM) approach. This alignment allows them to prioritize risk mitigation and consider the impact on reputation, resilience, compliance, and finances.
To learn more, read the NIST guide for Integrating Cybersecurity and Enterprise Risk Management.
For SAP, integrating cyber risks means assessing their effects on data breaches, operational downtime, financial losses, and reputation damage. This is how organizations can gain a comprehensive view and can develop cohesive mitigation strategies.
Quantifying cyber risks in SAP:
The confidentiality, integrity, and availability of information (CIA Triad) in an SAP system is often crucial to the operation of a business. Ideally, when the CIA Triad is effectively managed, the security profile of the organization is stronger and better equipped to handle threat incidents.
Let’s look at one real-life example on how Loss of Integrity could be estimated in an SAP environment (the specific values used in this example are for illustrative purposes only, and in practice, actual values would vary based on the organization and its context).
In this scenario, a privileged insider with malicious intent, could manipulate or alters data in the SAP systems, leading to a loss of integrity and potentially affecting product manufacturing processes.
Please note that, for the sake of simplicity, we will not delve into all the specific analysis parameters and variables, such as Control Frequency, Probability of Action, Threat Capability, and Resistance Strength.
We also present values as point estimates (for simplicity). In practice, we account for the uncertainty that naturally occurs in this work by using ranges of values. For example, threat event frequency might be estimated to be somewhere between 0.05 times per year (1 in 20 years) and 0.2 times per year (1 in 5 years) with a most likely of 0.1 times per year (1 in 10 years). In our examples, we’ll only discuss the single most likely value.
Threat Event Frequency:
Assume the threat of a Privileged Insider compromising the integrity of the SAP system occurs once every 10 years. Therefore, it would be 0.1.
Vulnerability Frequency:
Assume that the set of controls that protect from a skilled privileged insider from compromising the integrity of the SAP system only allow half of threat events to become loss events. Therefore, the probability that the Threat Event will result in a Loss Event could be estimated to 50%.
Primary Loss:
Consider the potential primary loss as the cost of rework, system restoration, and operational disruption caused by the compromised integrity of the SAP system. Assume this amounts to $500,000.
Secondary Loss:
Assume the secondary loss refers to the potential loss of customer trust, brand reputation, and market share. Assume a value of $30,000,000 was calculated to capture these intangible losses.
Loss Frequency:
Multiply the Threat Event Frequency (0.1) by the Vulnerability Frequency (50%) to calculate the Loss Frequency. In this case, it would be 0.05.
Loss Magnitude:
Add the Primary Loss and Secondary Loss together to get the Loss Magnitude. In this case, it would be $30,500,000 ($500,000 + $30,000,000).
Overall Risk:
Multiply the Loss Frequency by the Loss Magnitude to calculate the overall risk. In this case, the most likely annual aggregated loss exposure would be $152,500 ($30,500,000 * 0.05).
As previously stated, in practice, these values would also be expressed in ranges, as opposed to a single point value as shown in our example.
Call to Action:
This example demonstrates the importance of quantifying risk to help organizations see where they need to implement stronger access controls, monitoring mechanisms, privileged user management, and incident response protocols to maintain the integrity of their SAP systems and their business processes.
Quantifying cyber risk is an essential step towards building business resilience. The FAIR methodology empowers organizations to assign financial values to cyber risks, aiding in better decision-making and resource allocation.
However, the true power lies in integrating cyber risk management with the broader enterprise risk management framework, which allows organizations to get buy-in from senior leadership and effectively prioritize risks mitigations.
It is essential to acknowledge that cybersecurity is an ongoing investment that requires continuous adaptation and enhancement, and it is important to collaborate closely with your cloud service providers of software (SAAS), platform (PAAS), and infrastructure (IAAS) to fortify your organization against the ever-evolving face of cyber threats.
Learn more:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
Business Trends
145 -
Business Trends
15 -
Event Information
35 -
Event Information
9 -
Expert Insights
8 -
Expert Insights
29 -
Life at SAP
48 -
Product Updates
521 -
Product Updates
63 -
Technology Updates
196 -
Technology Updates
10
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |