
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by SAP
- SAP Reference architecture for IAM – Employee prov...
Enterprise Resource Planning Blogs by SAP
Get insights and updates about cloud ERP and RISE with SAP, SAP S/4HANA and SAP S/4HANA Cloud, and more enterprise management capabilities with SAP blog posts.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-02-2022
10:32 AM
One of the main challenges when we discuss architecture topics with customers and SAP partners is to discuss about security requirements, especially when we discuss Identity and Access Management (IAM) requirements.
The first requirement in almost all projects is to establish an authorization and single sign-on (SSO) strategy. My intention for this post it’s not to talk about basic authentication and SSO mechanisms, I take it for granted as there is plenty of tutorials and articles describing how to implement SSO in on-premise and/or hybrid landscapes.
Nevertheless, if you still haven’t implemented a SSO strategy, as a starting point let me recommend 2 excellent blogs from my colleagues:
I would like to focus on other aspects of the Identity and Access Management (IAM) that go beyond the basic authentication. As this is going to be a long post, I have divided the content in 3 parts:
Corporations are becoming more and more complex, the majority of customers have a mixture of on-premise and cloud applications and managing users on these hybrid environments poses challenging scenarios.
To add even more complexity, when we discuss about IAM we are discussing multiple topics. Under the umbrella of IAM we include different requirements that are tightly related:
All these topics are tightly related, you need to see the full picture, you cannot isolate each requirement individually. Unfortunately, when we discuss these requirements there are different people involved with different priorities and requirements and it’s not always easy to find a common ground to reach an agreement. Sadly, many projects in order to avoid these discussions decide to focus only on the easiest problem: authentication and SSO.
Don’t get me wrong, solving efficiently the authentication and SSO requirements is a huge step in the right direction but nowadays, SSO is far from being enough and we could consider SSO as the absolute minimum requirement.
I would like to focus on these other topics that are part of the IAM requirements and are less frequently discussed when we define a new architecture:
Before we start describing the recommended architecture, let me try to explain what is the problems we are trying to solve. One of the most common business challenges we see in many customers is the disconnection between the “HR world” and the “IT world”.
HR departments focus on new hires, promotions, sick leaves, people leaving the company… In the other hand, the IT department see users that must be created in the backend systems for a new employee, users that require specific authorizations depending on their business role and department, etc…
This disconnection between the HR world and the IT world generates a lot of ad-hoc workflows and manual procedures and is highly inefficient.
In this employee provisioning scenario, we will focus on how a customer running SAP SuccessFactors can integrate with Microsoft AD / ADFS or Azure AD to simplify the user provisioning. This is still a very simple scenario, offers authentication / SSO and user provisioning but still do not solve other requirements like role management, access governance or E2E integration.
Depending when the customer implemented SAP SuccessFactors there were different ways to setup the connection with an Identity Provider (IDP) to establish a SAML SSO:
The integration between SAP SuccessFactors and Microsoft AD / Azure AD have been improved over the years, depending when the customer did the configuration there were different options available:
3. Finally, in 2020, Microsoft together with SAP provide a new and better way to integrate SAP SuccessFactors with Azure AD and Microsoft AD via the new Azure AD user provisioning service
As you can see, customers can choose between different Identity Provider (IDP) configurations to provide SAML SSO and they can choose different methods to perform the integration between the SAP SuccessFactors and the IDP to enable the user provisioning.
The integration of SAP SuccessFactors with the IDP and their AD domains will enable 3 major data flows:
Integration between SAP SuccessFactors and the IDP – Authentication / SSO
As I mention before, the authentication / SSO via SAML, it’s not the main topic of this blog post as there is a huge number of blogs and articles describing this scenario in detail.
Integration between SAP SuccessFactors and the IDP – User Provisioning
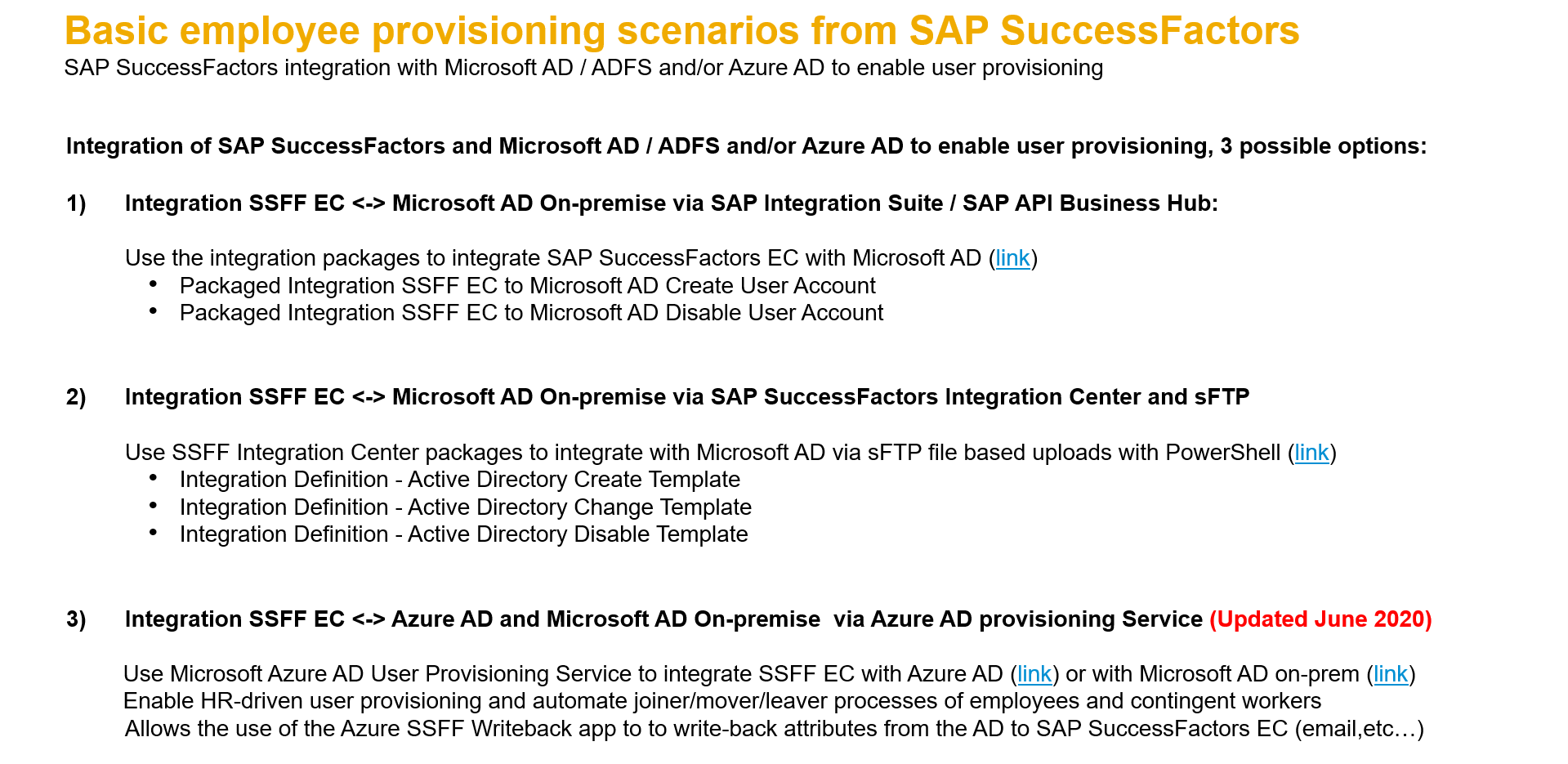
The user provisioning from SAP SuccessFactors to other systems is much more interesting and can be done via different methods described before:
The first method to integrate SAP SuccessFactors with Microsoft AD is via the SAP Integration Suite and with APIs from the SAP Business Hub. This is a very simple method and allows basic actions like create/change/delete users from SAP SuccessFactors to the AD.
For customers looking for a direct integration, without any other middleware, there was the option to use SAP SuccessFactors Integration Center with Windows PowerShell scripts and sFTP transfers.
The modern approach is the new Azure AD provisioning service, released in June 2020 by Microsoft in collaboration with SAP. This new provisioning service allows a better integration of SAP SuccessFactors with Azure AD for cloud only customers and/or with Microsoft AD for customers that still run their infrastructure on-premise.
With Azure AD provisioning service, customers can now setup HR-driven user provisioning from SAP SuccessFactors, so whenever an employee is created, updated, enabled, disabled in SAP SuccessFactors, that change can flow downstream to your corporate directory servers and to all your enterprise SaaS applications.
One of the key advantages of this solution is that it is completely cloud-native, what that means is that all the heavy lifting work of running the provisioning job, applying attribute mappings and managing the service execution is all handled in Azure AD.
You don’t need to deploy any on-premises identity management software. It provides out of the box support for several HR scenarios right from future hire provisioning to terminations. Once the identity is created in Azure AD, your enterprise SaaS apps connected to Azure AD will automatically get the data received from SAP SuccessFactors.
Azure AD Provisioning service include also a Writeback mode, that allows your IT admins to writeback IT managed attributes like email and phone number back to SAP SuccessFactors.
Integration between SAP SuccessFactors and the IDP – Attribute WriteBack
The last data flow between SAP SuccessFactors and the IDP is the Attribute Writeback. Not all the employee attributes are generated or managed in the SAP SuccessFactors system, some attributes like the employee email (Infotype 0105), phone number, Windows user name,etc… are generated and managed by the Active Directory (either Azure AD or Microsoft AD) and therefore must be “writeback” from the AD to the SAP SuccessFactors system.
Depending on the complexity of the landscape, the attribute writeback can be done via a direct integration between SAP SuccessFactors and Azure AD or indirectly via the Azure AD User provisioning service:
Azure AD Provisioning Service offers flexible mapping rules, can handle different HR scenarios and can retrieve 90+ pre-defined attributes or custom attributes.
With all the building blocks described before, we can finally assemble a reference architecture based on the Azure AD as the corporate IDP in combination with SAP SuccessFactors as the main HR system:
This architecture contains all the building blocks described before:
What is missing?
There is no authorization management, the users can be provisioned with a default role but you still need to assign the specific SAP roles to each user manually or via other tools.
There is no access governance, users are provisioned when there is an HR event but you cannot define policies to control when and which users are authorized to access the backend systems.
What else is missing?
In the diagram you see that we are using SAP Integration Suite to replicate the employee master data from SAP SuccessFactors to SAP S/4HANA and other backends. In order to run end-to-end scenarios like approval workflows between multiple systems, it is not enough to replicate the users, you still need the right master data in each system (e.g. employee cost center, BP number, etc...)
Customers can sync Master Data (Employee and Org. Data) via integration packages from the SAP Integration Suite:
Summary and next steps
In this first blog post, we described how frequently customers and projects focus on the authentication and SSO requirements and ignore or postpone the implementation of other important IAM requirements like user provisioning, authorization management, access governance or End-to-End integration between systems.
We described in detail the reference architecture for customers running SAP SuccessFactors integrated with Azure AD and/or Microsoft AD/ADFS as this is a very popular scenario among our SAP customers. Despite being a very simple scenario, the integration with Azure AD offers authentication and SSO but also offers employee provisioning via the Azure AD provisioning service.
In my next 2 blog posts I will discuss in detail what are the benefits of using SAP Identity and Authentication Service (IAS) as an standalone IDP or as a proxy of the corporate IDP and also more advanced scenarios that offer better end-to-end integration between SAP applications:
stay tuned!
Brought to you by the SAP S/4HANA RIG and Customer Care team.
The first requirement in almost all projects is to establish an authorization and single sign-on (SSO) strategy. My intention for this post it’s not to talk about basic authentication and SSO mechanisms, I take it for granted as there is plenty of tutorials and articles describing how to implement SSO in on-premise and/or hybrid landscapes.
Nevertheless, if you still haven’t implemented a SSO strategy, as a starting point let me recommend 2 excellent blogs from my colleagues:
- Single Sign-on: SAP Reference Architecture for Identity Access Management
- Single Sign-On Guide for SAP S/4HANA Cloud, Private Edition (RISE with SAP)
I would like to focus on other aspects of the Identity and Access Management (IAM) that go beyond the basic authentication. As this is going to be a long post, I have divided the content in 3 parts:
- SAP Reference architecture for IAM – Employee provisioning with Azure AD (this post)
- SAP Reference architecture for IAM – Employee provisioning with SAP IAS
- SAP Reference architecture for IAM – HR Driven identity lifecycle management - Recruit-to-Retire
Identity and Access Management requirements
Corporations are becoming more and more complex, the majority of customers have a mixture of on-premise and cloud applications and managing users on these hybrid environments poses challenging scenarios.
To add even more complexity, when we discuss about IAM we are discussing multiple topics. Under the umbrella of IAM we include different requirements that are tightly related:
- Authentication and SSO
- User management and user provisioning
- Authorizations and role management
- Access Governance
- E2E Integration
All these topics are tightly related, you need to see the full picture, you cannot isolate each requirement individually. Unfortunately, when we discuss these requirements there are different people involved with different priorities and requirements and it’s not always easy to find a common ground to reach an agreement. Sadly, many projects in order to avoid these discussions decide to focus only on the easiest problem: authentication and SSO.
Don’t get me wrong, solving efficiently the authentication and SSO requirements is a huge step in the right direction but nowadays, SSO is far from being enough and we could consider SSO as the absolute minimum requirement.
I would like to focus on these other topics that are part of the IAM requirements and are less frequently discussed when we define a new architecture:
- User management - How users will be provisioned in each system
- Authorization management - How authorizations will be assigned to each user
- Access Governance - How you can establish policies to control who access the systems
- E2E integration - How you run end-to-end processes across multiple systems
Employee provisioning scenarios – Key elements
Before we start describing the recommended architecture, let me try to explain what is the problems we are trying to solve. One of the most common business challenges we see in many customers is the disconnection between the “HR world” and the “IT world”.
HR departments focus on new hires, promotions, sick leaves, people leaving the company… In the other hand, the IT department see users that must be created in the backend systems for a new employee, users that require specific authorizations depending on their business role and department, etc…
This disconnection between the HR world and the IT world generates a lot of ad-hoc workflows and manual procedures and is highly inefficient.
In this employee provisioning scenario, we will focus on how a customer running SAP SuccessFactors can integrate with Microsoft AD / ADFS or Azure AD to simplify the user provisioning. This is still a very simple scenario, offers authentication / SSO and user provisioning but still do not solve other requirements like role management, access governance or E2E integration.

HR world vs IT world
Depending when the customer implemented SAP SuccessFactors there were different ways to setup the connection with an Identity Provider (IDP) to establish a SAML SSO:
- Initially, SAP SuccessFactors had an internal IDP
- Some time later, we added support for Microsoft AD / ADFS and other 3rd party IDPs.
- Then, support for the SAP Identity and Authentication Service (IAS)
- Lately, many customer choose Azure AD.
The integration between SAP SuccessFactors and Microsoft AD / Azure AD have been improved over the years, depending when the customer did the configuration there were different options available:
- First, there was a very simple integration package to integrate SAP SuccessFactors EC with Microsoft AD (link)

2. Later, a SAP SuccessFactors Integration Center packages to integrate with Microsoft AD via sFTP file based uploads with PowerShell (link) was introduced for customers looking for a simple integration without any additional middleware:

3. Finally, in 2020, Microsoft together with SAP provide a new and better way to integrate SAP SuccessFactors with Azure AD and Microsoft AD via the new Azure AD user provisioning service

As you can see, customers can choose between different Identity Provider (IDP) configurations to provide SAML SSO and they can choose different methods to perform the integration between the SAP SuccessFactors and the IDP to enable the user provisioning.
Why is it important to integrate SAP SuccessFactors with an Identity Provider (IDP)?
The integration of SAP SuccessFactors with the IDP and their AD domains will enable 3 major data flows:
- Authentication / SSO via SAML
- User Provisioning from SAP SuccessFactors to other systems
- Attribute Writeback from AD back to SAP SAP SuccessFactors / HCM (Infotype 0105 / email)
Integration between SAP SuccessFactors and the IDP – Authentication / SSO
As I mention before, the authentication / SSO via SAML, it’s not the main topic of this blog post as there is a huge number of blogs and articles describing this scenario in detail.
Integration between SAP SuccessFactors and the IDP – User Provisioning
The user provisioning from SAP SuccessFactors to other systems is much more interesting and can be done via different methods described before:
SSFF Integration with AD to enable user provisioning
The first method to integrate SAP SuccessFactors with Microsoft AD is via the SAP Integration Suite and with APIs from the SAP Business Hub. This is a very simple method and allows basic actions like create/change/delete users from SAP SuccessFactors to the AD.
For customers looking for a direct integration, without any other middleware, there was the option to use SAP SuccessFactors Integration Center with Windows PowerShell scripts and sFTP transfers.
The modern approach is the new Azure AD provisioning service, released in June 2020 by Microsoft in collaboration with SAP. This new provisioning service allows a better integration of SAP SuccessFactors with Azure AD for cloud only customers and/or with Microsoft AD for customers that still run their infrastructure on-premise.
With Azure AD provisioning service, customers can now setup HR-driven user provisioning from SAP SuccessFactors, so whenever an employee is created, updated, enabled, disabled in SAP SuccessFactors, that change can flow downstream to your corporate directory servers and to all your enterprise SaaS applications.
One of the key advantages of this solution is that it is completely cloud-native, what that means is that all the heavy lifting work of running the provisioning job, applying attribute mappings and managing the service execution is all handled in Azure AD.
You don’t need to deploy any on-premises identity management software. It provides out of the box support for several HR scenarios right from future hire provisioning to terminations. Once the identity is created in Azure AD, your enterprise SaaS apps connected to Azure AD will automatically get the data received from SAP SuccessFactors.

Azure AD provisioning Service
Azure AD Provisioning service include also a Writeback mode, that allows your IT admins to writeback IT managed attributes like email and phone number back to SAP SuccessFactors.
Integration between SAP SuccessFactors and the IDP – Attribute WriteBack
The last data flow between SAP SuccessFactors and the IDP is the Attribute Writeback. Not all the employee attributes are generated or managed in the SAP SuccessFactors system, some attributes like the employee email (Infotype 0105), phone number, Windows user name,etc… are generated and managed by the Active Directory (either Azure AD or Microsoft AD) and therefore must be “writeback” from the AD to the SAP SuccessFactors system.
Depending on the complexity of the landscape, the attribute writeback can be done via a direct integration between SAP SuccessFactors and Azure AD or indirectly via the Azure AD User provisioning service:

Azure AD Provisioning Service offers flexible mapping rules, can handle different HR scenarios and can retrieve 90+ pre-defined attributes or custom attributes.
Reference architecture for employee provisioning scenarios with Azure AD as the corporate IDP
With all the building blocks described before, we can finally assemble a reference architecture based on the Azure AD as the corporate IDP in combination with SAP SuccessFactors as the main HR system:

Reference architecture for employee provisioning scenarios with SAP Success Factors and Azure AD / Microsoft ADFS as corporate IdP
This architecture contains all the building blocks described before:
- Azure AD with/without Microsoft AD + ADFS as the corporate Identity Provider.
- Provides authentication and SSO via SAML for SAP Fiori and web / cloud applications
- It also offers SAP GUI SSO via Kerberos and SPNEGO for Web connections.
- User provisioning from SAP SuccessFactors and support multiple HR scenarios.
- And offers predefined or custom attribute writeback from AD back to SAP SuccessFactors.
What is missing?
There is no authorization management, the users can be provisioned with a default role but you still need to assign the specific SAP roles to each user manually or via other tools.
There is no access governance, users are provisioned when there is an HR event but you cannot define policies to control when and which users are authorized to access the backend systems.
What else is missing?
In the diagram you see that we are using SAP Integration Suite to replicate the employee master data from SAP SuccessFactors to SAP S/4HANA and other backends. In order to run end-to-end scenarios like approval workflows between multiple systems, it is not enough to replicate the users, you still need the right master data in each system (e.g. employee cost center, BP number, etc...)
Customers can sync Master Data (Employee and Org. Data) via integration packages from the SAP Integration Suite:

Master Data replication
Summary and next steps
In this first blog post, we described how frequently customers and projects focus on the authentication and SSO requirements and ignore or postpone the implementation of other important IAM requirements like user provisioning, authorization management, access governance or End-to-End integration between systems.
We described in detail the reference architecture for customers running SAP SuccessFactors integrated with Azure AD and/or Microsoft AD/ADFS as this is a very popular scenario among our SAP customers. Despite being a very simple scenario, the integration with Azure AD offers authentication and SSO but also offers employee provisioning via the Azure AD provisioning service.
In my next 2 blog posts I will discuss in detail what are the benefits of using SAP Identity and Authentication Service (IAS) as an standalone IDP or as a proxy of the corporate IDP and also more advanced scenarios that offer better end-to-end integration between SAP applications:
- SAP Reference architecture for IAM – Employee provisioning with Azure AD (this post)
- SAP Reference architecture for IAM – Employee provisioning with SAP IAS
- SAP Reference architecture for IAM – HR Driven identity lifecycle management - Recruit-to-Retire
stay tuned!
Brought to you by the SAP S/4HANA RIG and Customer Care team.
Labels:
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Artificial Intelligence (AI)
1 -
Business Trends
363 -
Business Trends
24 -
Customer COE Basics and Fundamentals
1 -
Digital Transformation with Cloud ERP (DT)
1 -
Event Information
461 -
Event Information
24 -
Expert Insights
114 -
Expert Insights
160 -
General
1 -
Governance and Organization
1 -
Introduction
1 -
Life at SAP
415 -
Life at SAP
2 -
Product Updates
4,684 -
Product Updates
220 -
Roadmap and Strategy
1 -
Technology Updates
1,502 -
Technology Updates
89
Related Content
- Quick Start guide for PLM system integration 3.0 Implementation/Installation in Enterprise Resource Planning Blogs by SAP
- FAQ on Upgrading SAP S/4HANA Cloud Public Edition in Enterprise Resource Planning Blogs by SAP
- SAP S/4HANA Service and integration with SAP Field Service Management in Enterprise Resource Planning Blogs by SAP
- Deletion of Master and Transactional Data (ILM) in SAP S/4HANA Cloud,Public Edition-Link Collection in Enterprise Resource Planning Blogs by SAP
- New Reference Solution Architecture for SAP Master Data Governance in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 11 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 4 | |
| 4 |