
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by Members
- SAP S4/Hana ABAP RFC connection via SNC
Enterprise Resource Planning Blogs by Members
Gain new perspectives and knowledge about enterprise resource planning in blog posts from community members. Share your own comments and ERP insights today!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
anikesh_jyotish
Participant
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-02-2022
5:35 PM
Overview
Under this blog I have outlined ABAP RFC connection via SNC, so we have used RFC with SNC (Secure Network Communications)2.0 setup.
SNC is a software layer in the SAP system that provides an interface to an external security product. SNC, you can strengthen the security of your SAP system by implementing additional security functions that SAP systems do not directly provide.
Dia from help.sap.com
DISCLAIMER
The content of this blog post is provided “AS IS”. This information could contain technical inaccuracies, typographical errors, and out-of-date information. This document may be updated or changed without notice at any time. Use of the information is therefore at your own risk. In no event shall SAP be liable for special, indirect, incidental, or consequential damages resulting from or related to the use of this document.
Purpose
This document tried to include all Basis steps for enabling SNC for ABAP RFCs for secure connections.
SAP S4/Hana ABAP connection via SNC
Steps: –
• Setup SNC in both systems
• Generate SNC certificate from both systems and map in strustsso2 SNC SAPCryptolib
• Create a user (sidadm or any name) in AD Users and update service principal name same as SNC cert in Attribute Editor (SAP/ SNC certificate name) as per note 1696905 (Optional if you are using AD connection)
• ACL mode either 0 or whitelist hostname
• Update SNC0 with target system certificate details
• Update SM54 with the destination
• Verify SM30 VSNCSYSACL (I= internal and E= external) systems SNC cert name
• Create RFC with SNC config and test
Setup SNC in both systems
We will use SNCWIZARD for SNC setup
Check all SNC-related parameters below
In the below screen, it will give all your instance details which need to restart.
If you do not want to configure Kerberos credentials, choose Skip
We will use this cert for RFC communication
Strustsso2
Repeat the same steps in the target system
Check all SNC parameters in the default profile
snc/accept_insecure_cpic = 1
snc/accept_insecure_gui = 1
snc/accept_insecure_rfc = 1
snc/data_protection/max = 2
snc/data_protection/min = 1
snc/enable = 1
snc/gssapi_lib = $(SAPCRYPTOLIB)
snc/identity/as = SNC cer name
snc/permit_insecure_start = 1
spnego/enable = 1
Restart the application server
After restart check SNC status via SM51 SNC check
SNC certificate from both systems and map in strustsso2 (SNC SAPCryptolib)
Goto strustsso2:- below certificate generated during SNC setup. Click on edit and export below certificate as base64 and import into target system (Repeat same steps in target system)
ACL mode either 0 or whitelist hostname
Gateway ACL mode 0
The following values are possible:
0: There is no restriction with starting external servers or registering servers. This setting should not be used in production operations.
1: External and registered servers are only permitted within the system (application servers of the same system). All other servers are rejected or have to be maintained in the respective files.
The default value of the parameter is 1.
If you are using 1 then go to SMGW and allow the target hostname.
SMGW Goto expert functions external security maintain ACL list (secinfo and reginfo)
Update SNC0 with target system cert details
Update target system SID and SNC certificate details with p: (update SNC canonical name)
Active entry for RFC, entry for CPIC, Entry for the certificate (same on the target system)
The SNCSYSACL entries that you make using transaction SNC0 are saved as external RFC destinations (type = E). Internal destinations (type = I) are automatically generated and not shown in transaction SNC0.
Update SM54 with the destination
Update destination SID, login type I, and update target SNC cert name with p: It will update the VSNCSYSACL table.
Verify SM30 VSNCSYSACL (I= internal and E= external) systems SNC cert name
Go to SM30 give table name as VSNCSYSACL click on display
Give work area as I for internal system
Go back and give the work area as E for the External system
Create RFC with SNC config and test
Create type 3 RFC, Give RFC destination name and description
Go to logon security and give the target system user id.
On the same page activate SNC
Perform connection and authorization test
Reference SAP Notes:-
https://help.sap.com/docs/SAP_NETWEAVER_740/621bb4e3951b4a8ca633ca7ed1c0aba2/aa38ff4fa187622fe100000...
2653733 - Enabling SNC on RFCs between AS ABAP
https://help.sap.com/saphelp_nwpi71/helpdata/en/28/03f4ad8d9d490c99a3e8a57551d264/frameset.htm
Advantages:-
1. Help to secure RFC connection
I hope this document will help you with the RFC setup via SNC.
Cheers!
Anikesh Jyotishi
Under this blog I have outlined ABAP RFC connection via SNC, so we have used RFC with SNC (Secure Network Communications)2.0 setup.
SNC is a software layer in the SAP system that provides an interface to an external security product. SNC, you can strengthen the security of your SAP system by implementing additional security functions that SAP systems do not directly provide.

Dia from help.sap.com
DISCLAIMER
The content of this blog post is provided “AS IS”. This information could contain technical inaccuracies, typographical errors, and out-of-date information. This document may be updated or changed without notice at any time. Use of the information is therefore at your own risk. In no event shall SAP be liable for special, indirect, incidental, or consequential damages resulting from or related to the use of this document.
Purpose
This document tried to include all Basis steps for enabling SNC for ABAP RFCs for secure connections.
SAP S4/Hana ABAP connection via SNC
Steps: –
• Setup SNC in both systems
• Generate SNC certificate from both systems and map in strustsso2 SNC SAPCryptolib
• Create a user (sidadm or any name) in AD Users and update service principal name same as SNC cert in Attribute Editor (SAP/ SNC certificate name) as per note 1696905 (Optional if you are using AD connection)
• ACL mode either 0 or whitelist hostname
• Update SNC0 with target system certificate details
• Update SM54 with the destination
• Verify SM30 VSNCSYSACL (I= internal and E= external) systems SNC cert name
• Create RFC with SNC config and test
Setup SNC in both systems
We will use SNCWIZARD for SNC setup

Check all SNC-related parameters below

In the below screen, it will give all your instance details which need to restart.

If you do not want to configure Kerberos credentials, choose Skip
We will use this cert for RFC communication

Strustsso2

Repeat the same steps in the target system
Check all SNC parameters in the default profile
snc/accept_insecure_cpic = 1
snc/accept_insecure_gui = 1
snc/accept_insecure_rfc = 1
snc/data_protection/max = 2
snc/data_protection/min = 1
snc/enable = 1
snc/gssapi_lib = $(SAPCRYPTOLIB)
snc/identity/as = SNC cer name
snc/permit_insecure_start = 1
spnego/enable = 1
Restart the application server
After restart check SNC status via SM51 SNC check

SNC certificate from both systems and map in strustsso2 (SNC SAPCryptolib)
Goto strustsso2:- below certificate generated during SNC setup. Click on edit and export below certificate as base64 and import into target system (Repeat same steps in target system)


ACL mode either 0 or whitelist hostname
Gateway ACL mode 0
The following values are possible:
0: There is no restriction with starting external servers or registering servers. This setting should not be used in production operations.
1: External and registered servers are only permitted within the system (application servers of the same system). All other servers are rejected or have to be maintained in the respective files.
The default value of the parameter is 1.

If you are using 1 then go to SMGW and allow the target hostname.
SMGW Goto expert functions external security maintain ACL list (secinfo and reginfo)
Update SNC0 with target system cert details
Update target system SID and SNC certificate details with p: (update SNC canonical name)
Active entry for RFC, entry for CPIC, Entry for the certificate (same on the target system)

The SNCSYSACL entries that you make using transaction SNC0 are saved as external RFC destinations (type = E). Internal destinations (type = I) are automatically generated and not shown in transaction SNC0.
Update SM54 with the destination
Update destination SID, login type I, and update target SNC cert name with p: It will update the VSNCSYSACL table.

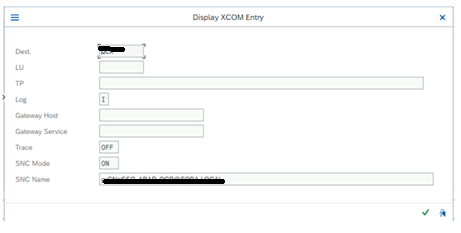
Verify SM30 VSNCSYSACL (I= internal and E= external) systems SNC cert name
Go to SM30 give table name as VSNCSYSACL click on display
Give work area as I for internal system


Go back and give the work area as E for the External system

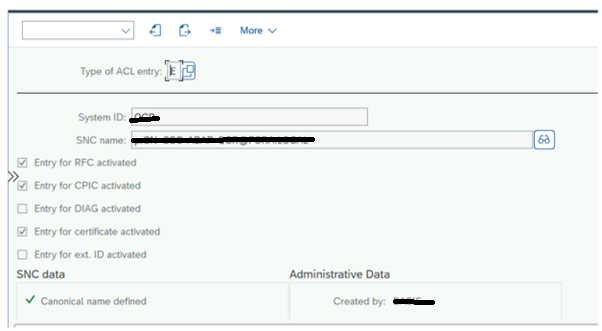
Create RFC with SNC config and test
Create type 3 RFC, Give RFC destination name and description

Go to logon security and give the target system user id.

On the same page activate SNC


Perform connection and authorization test

Reference SAP Notes:-
https://help.sap.com/docs/SAP_NETWEAVER_740/621bb4e3951b4a8ca633ca7ed1c0aba2/aa38ff4fa187622fe100000...
2653733 - Enabling SNC on RFCs between AS ABAP
https://help.sap.com/saphelp_nwpi71/helpdata/en/28/03f4ad8d9d490c99a3e8a57551d264/frameset.htm
Advantages:-
1. Help to secure RFC connection
I hope this document will help you with the RFC setup via SNC.
Cheers!
Anikesh Jyotishi
- SAP Managed Tags:
- SAP ERP Central Component,
- SAP S/4HANA
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"mm02"
1 -
A_PurchaseOrderItem additional fields
1 -
ABAP
1 -
ABAP Extensibility
1 -
ACCOSTRATE
1 -
ACDOCP
1 -
Adding your country in SPRO - Project Administration
1 -
Advance Return Management
1 -
AI and RPA in SAP Upgrades
1 -
Approval Workflows
1 -
Ariba
1 -
ARM
1 -
ASN
1 -
Asset Management
1 -
Associations in CDS Views
1 -
auditlog
1 -
Authorization
1 -
Availability date
1 -
Azure Center for SAP Solutions
1 -
AzureSentinel
2 -
Bank
1 -
BAPI_SALESORDER_CREATEFROMDAT2
1 -
BRF+
1 -
BRFPLUS
1 -
Bundled Cloud Services
1 -
business participation
1 -
Business Processes
1 -
CAPM
1 -
Carbon
1 -
Cental Finance
1 -
CFIN
1 -
CFIN Document Splitting
1 -
Cloud ALM
1 -
Cloud Integration
1 -
condition contract management
1 -
Connection - The default connection string cannot be used.
1 -
Custom Table Creation
1 -
Customer Screen in Production Order
1 -
Data Quality Management
1 -
Date required
1 -
Decisions
1 -
desafios4hana
1 -
Developing with SAP Integration Suite
1 -
Direct Outbound Delivery
1 -
DMOVE2S4
1 -
EAM
1 -
EDI
3 -
EDI 850
1 -
EDI 856
1 -
edocument
1 -
EHS Product Structure
1 -
Emergency Access Management
1 -
Energy
1 -
EPC
1 -
Financial Operations
1 -
Find
1 -
FINSSKF
1 -
Fiori
1 -
Flexible Workflow
1 -
Gas
1 -
Gen AI enabled SAP Upgrades
1 -
General
1 -
generate_xlsx_file
1 -
Getting Started
1 -
HomogeneousDMO
1 -
How to add new Fields in the Selection Screen Parameter in FBL1H Tcode
1 -
IDOC
2 -
Integration
1 -
Learning Content
2 -
LogicApps
2 -
low touchproject
1 -
Maintenance
1 -
management
1 -
Material creation
1 -
Material Management
1 -
MD04
1 -
MD61
1 -
methodology
1 -
Microsoft
2 -
MicrosoftSentinel
2 -
Migration
1 -
mm purchasing
1 -
MRP
1 -
MS Teams
2 -
MT940
1 -
Newcomer
1 -
Notifications
1 -
Oil
1 -
open connectors
1 -
Order Change Log
1 -
ORDERS
2 -
OSS Note 390635
1 -
outbound delivery
1 -
outsourcing
1 -
PCE
1 -
Permit to Work
1 -
PIR Consumption Mode
1 -
PIR's
1 -
PIRs
1 -
PIRs Consumption
1 -
PIRs Reduction
1 -
Plan Independent Requirement
1 -
Premium Plus
1 -
pricing
1 -
Primavera P6
1 -
Process Excellence
1 -
Process Management
1 -
Process Order Change Log
1 -
Process purchase requisitions
1 -
Product Information
1 -
Production Order Change Log
1 -
purchase order
1 -
Purchase requisition
1 -
Purchasing Lead Time
1 -
Redwood for SAP Job execution Setup
1 -
RISE with SAP
1 -
RisewithSAP
1 -
Rizing
1 -
S4 Cost Center Planning
1 -
S4 HANA
1 -
S4HANA
3 -
Sales and Distribution
1 -
Sales Commission
1 -
sales order
1 -
SAP
2 -
SAP Best Practices
1 -
SAP Build
1 -
SAP Build apps
1 -
SAP Cloud ALM
1 -
SAP Data Quality Management
1 -
SAP Maintenance resource scheduling
2 -
SAP Note 390635
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud private edition
1 -
SAP Upgrade Automation
1 -
SAP WCM
1 -
SAP Work Clearance Management
1 -
Schedule Agreement
1 -
SDM
1 -
security
2 -
Settlement Management
1 -
soar
2 -
Sourcing and Procurement
1 -
SSIS
1 -
SU01
1 -
SUM2.0SP17
1 -
SUMDMO
1 -
Teams
2 -
User Administration
1 -
User Participation
1 -
Utilities
1 -
va01
1 -
vendor
1 -
vl01n
1 -
vl02n
1 -
WCM
1 -
X12 850
1 -
xlsx_file_abap
1 -
YTD|MTD|QTD in CDs views using Date Function
1
- « Previous
- Next »
Related Content
- Building Low Code Extensions with Key User Extensibility in SAP S/4HANA and SAP Build in Enterprise Resource Planning Blogs by SAP
- Business Rule Framework Plus(BRF+) in Enterprise Resource Planning Blogs by Members
- SAP ERP Functionality for EDI Processing: UoMs Determination for Inbound Orders in Enterprise Resource Planning Blogs by Members
- SAP S/4HANA Cloud Extensions with SAP Build Best Practices: An Expert Roundtable in Enterprise Resource Planning Blogs by SAP
- Redwood RMJ Architecture, Integration and Interface review with SAP S/4 HANA and ECC Job execution. in Enterprise Resource Planning Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |