- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Cloud Integration: Advanced Event Mesh Adapter, Cl...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SAP Cloud Integration (aka CPI) offers an “Advanced Event Mesh Adapter” which is well integrated with the “Advanced Event Mesh” broker.
This article shows how to set up a scenario where we send a message from iFlow via “Advanced Event Mesh Adapter” to SAP Cloud Integration, Advanced Event Mesh (AEM) with Client Certificate Authentication.
Please refer to the sibling article series which describes in detail the setup for "AMQP Adapter".
The creation of a certificate chain is equal in both scenarios.
The configuration in AEM is also same as in Solace.
So basically, in this blog post we only need to show the configuration in the “Advanced Event Mesh” (AEM) adapter.
Overview
- Introduction
- Create Client Certificate
- Configure AEM
- Create iFlow
- Run Scenario
- Key Takeaways
Prerequisites
🔹To follow this tutorial, access to SAP Advanced Event Mesh is required.
🔹Access To CPI Tenant is required
🔹I recommend bookmarking the Security Glossary
1. Introduction
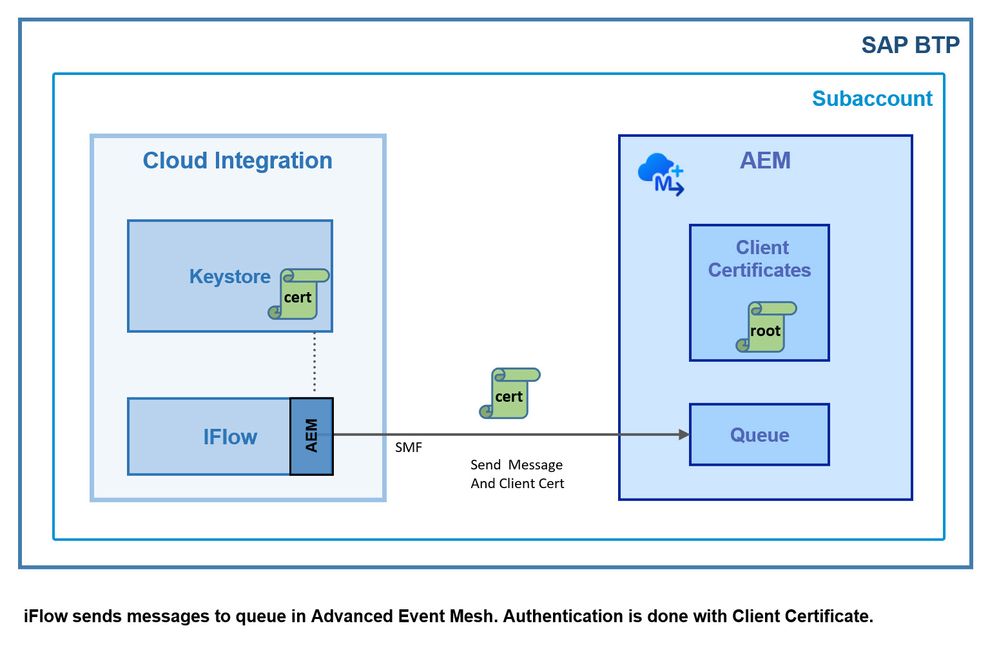
We want to send a message from an iFlow to Advanced Event Mesh Broker.
We want to use the “Advanced Event Mesh” adapter.
Authentication should be configured with client certificate.
There’s a sibling blog post which uses the AMQP adapter for the same use case.
Almost all steps are equal and described in detail there.
What is the scenario?
This is the high-level overview of the simple scenario:
We can see that the iFlow sends messages via "Advanced Event Mesh adapter" to a queue in Advanced Event Mesh.
On both sides, certificates have to be configured.
How to get certificates?
The sibling article series explains in detail multiple ways of generating certificates for this purpose.
To give an overview of some possibilities:
🔷Use CPI Keystore dashboard
1. Create key pair / certificate in CPI
🔹Use it as self-signed root in our scenario
🔹Download the corresponding CSR (certificate signing request) and create a self-signed chain on laptop
🔹Download the CSR and use it to purchase a productive chain from productive CA
2. Download existing CPI client certificate chain and use it for our scenario
🔷Use Laptop
-> Create key pair / certificate ourselves on laptop
🔹Use Openssl
- Create self-signed root or chain (chain with different length)
- Create CSR and purchase productive chain
🔹Use Java Keytool
- etc
🔹Use any other tool
- etc
🔷Use BTP
-> let service broker or IAs generate key pair / certificate chain and use that for our scenario
Alternatively, there are tools in the internet and for download, to handle such tasks.
In the present tutorial, we’re going the easy way and use a CPI-generated certificate.
I recommend however going through the experience of creating certificate chain on local computer.
2. Create Client Certificate
Using the built-in functionality of CPI to generate a key pair has the following advantage:
The private key is generated at CPI, where it is needed.
The private key never leaves CPI (it is not possible to download it)
The private key does not need to be uploaded to CPI via net.
The disadvantage would be that this private key cannot be used locally, as it is not possible to download it.
For today’s article, we’re using the CPI keystore to create a self-signed certificate.
This will serve as trusted root certificate at AEM-side, and it will be used as client-certificate in iFlow.
Ceate Key Pair in CPI
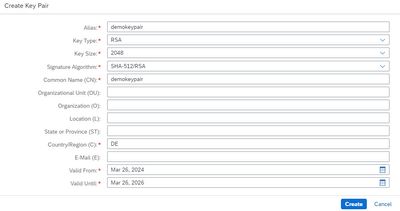
We go to keystore and choose "Create -> Key Pair"
We enter some data of your choice, e.g.
🔸Alias: “demokeypair”
🔸CN: “demokeypair”
It will be used for creating the certificate.
After creation, we click on the new entry I the dashboard to view the details:
We can see that a self-signed certificate has been created.
If subject and issuer DN are equal, then this means it is a root certificate.
Now we can download the new certificate via context button and “Download Certificate”
In my example, a file demokeypair.cer is downloaded to my laptop.
Note:
If you encounter a .p7b file after download artifacts, you can extract it with the help of OpenSSL and the pkcs7 command.
openssl pkcs7 -in demokeypair.p7b -print_certs -out certificate.cer
3. Configure Advanced Event Mesh
Now that we have the client certificate, we can establish trust at AEM side.
This means:
AEM receives an authentication request with a client certificate.
It must validate the certificate.
It must trust it.
To do so, the signature of the issuer is checked – and the issuer itself – continuing the chain up to the root.
If the root is not known by AEM, then it has to be configured.
As such, we have to upload our certificate (which is a root as well) to AEM.
See sibling blog post for detailed description.
3.1. Upload Root Certificate
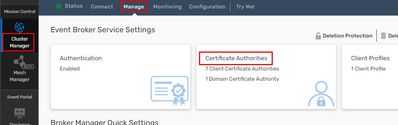
We go to “Cluster Manager” ➡️ Event Broker service instance ➡️ “Manage” tab.
➡️click “Certificate Authorities” and upload the root certificate from previous chapter.
In my example, we upload the demokeypair.cer file.
3.2. Authorization for Client
We go to “Cluster Manager” ➡️ Event Broker service instance ➡️ “Open Broker Manager”.
➡️ “Access Control” ➡️ “Client Usernames”.
Create new client username and enter the value of the “CN” of our client certificate from previous chapter.
In my example: “demokeypair”
➡️ Press “Create”.
➡️ Press “Enable”.
➡️ Press “Apply”.
3.3. Create Queue
We're still in the “Broker Manager”, so now we choose “Queues” on the left navigation pane.
Then we create a new queue and enter a name of our choice, e.g. “demo”
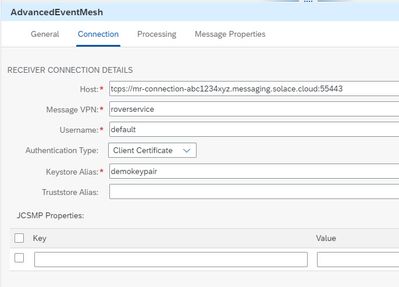
3.4. Connection Details
To find the connection details that we need in the next chapter, we go to
“Cluster Manager” ➡️ Event Broker service instance ➡️ “Connect” tab.
Expand “Solace Messaging” section (SMF over TCP).
Copy the “Message VPN” and “SMF Host”:
4. Create iFlow
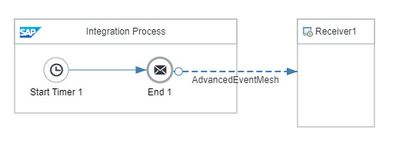
We create a very simple iFlow that does nothing than sending an empty message to Advanced Event Mesh.
See sibling blog post for some more description.
Other than in sibling post, we use the “Advanced Event Mesh” adapter.
Configure Advanced Event Mesh adapter
🔸URL
We need to enter the full URL of the SMF host, which we copied in previous chapter.
Including protocol and port.
Just copy&paste from AEM dashboard (previous chapter).
🔸Message VPN
The Message VPN can also be copied from AEM.
🔸Username
The Username “default” can be used, as it is available on AEM as per default.
But any other existing username can be entered here as well.
🔸Keystore Alias
The Keystore Alias must point to a key pair entry.
It is checked during deployment.
In our example, we enter the key pair which we created in chapter above: “demokeypair”
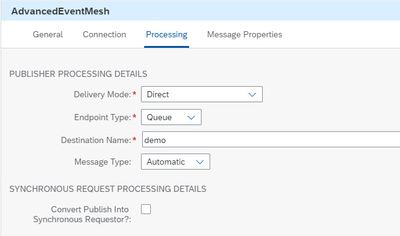
In the “Processing” Tab, we choose “Queue” and enter the name of the queue we created above:
That’s it, we can save the iFlow.
5. Run Scenario
To run the scenario we just deploy the iFlow.
Then we check the result:
In CPI : The log at “Monitor Message Processing” should show success message.
In event broker: The number of “Messages Queued” should have increased.
6. Quick Guide
🔷Certificate Chain:
🔹The intermediate certificate must have CA:TRUE
🔹The chain order: Root Rear.
🔷AEM:
🔹Upload the root cert.
🔹Create username equal to “CN”.
🔹Username must be set to "Enabled".
🔷CPI:
🔹Upload the chain, not only client cert.
Reason: the whole chain must be sent to AEM, as at AEM only the root is known.
Summary
In this blog post we’ve learned how to deal with client certificates.
We wanted to use certificate-based authentication instead of username / password (Basic Auth).
To do so, we learned how to easily get a key pair and a certificate.
To establish trust, we need to configure the target server (AEM) with the trusted root certificate.
Finally, we can use the certificate in CPI, which means, it is stored in the Keystore and used in the iflow.
In this blog post, we’ve learned how to configure the Advanced Event Mesh adapter.
There’s a sibling article series which explains many details about certificates.
Links
SAP Help Portal landing page : https://help.sap.com/docs/SAP_ADVANCED_EVENT_MESH
Documentation entry page: https://help.pubsub.em.services.cloud.sap/Cloud/cloud-lp.htm
🎉🎉🎉🎉🎉🎉🎉
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
429 -
Workload Fluctuations
1
- External System Integration in DMC in Technology Blogs by Members
- Enhance your SAP Datasphere Experience with API Access in Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Exploring Integration Options in SAP Datasphere with the focus on using SAP extractors - Part II in Technology Blogs by SAP
- FAQ for C4C Certificate Renewal in Technology Blogs by SAP
| User | Count |
|---|---|
| 34 | |
| 17 | |
| 15 | |
| 14 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |