- SAP Community
- Products and Technology
- Technology
- Technology Q&A
- "401 Not authorized" in FLP configured to use cust...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
"401 Not authorized" in FLP configured to use custom IdP (SAML2.0 config)
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 12-02-2019 8:49 PM
Hello experts!
I've configured a custom IdP in SAP Cloud Platform for authenticate users with a SAML2.0 based IdP called Access Manager, but I'm getting "401 Not Authorized" when accesing the specified URL in the Access Manager configuration. I'll depict to you the steps I've performed:
1. Config SAP Cloud Platform as Service Provider under Security --> Trust.

2. Download and send metadata to Access Manager IdP (the IdP team already did what it's required with the metadata in the IdP side).

3. Charge up the IdP metatada in "Application Identity Provider" tab.

4. Generated default group.
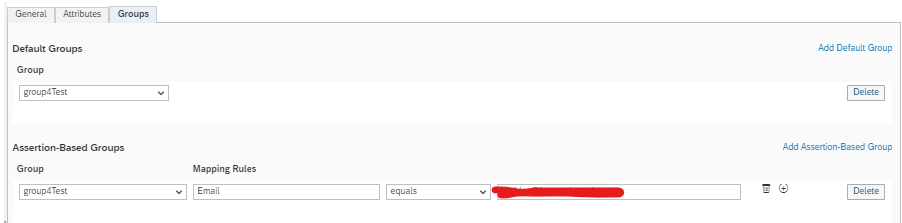
Note: the assertion rule says: "Email equals myemail@mycompany.com" and that's the user I'm using to test.
5. Attributes (I'm not sure this is necessary):

And that's it.
------------------------------------------------------------------------------------------------------------------------------------
Then I have the following errors when trying to log in: 401 Not Authorized
And this is the info displayed in the SAML trace:

In the SAML tab:
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
Destination="https://flpnwc-irpfpd5ihm.dispatcher.us2.hana.ondemand.com/sites/testingsite#Shell-home"
ID="idKH-VJOB9yxGCJF4a4WHWqaLIhWE"
IssueInstant="2019-12-02T17:36:29Z"
Version="2.0"
>
<saml:Issuer>https://login.customer.com/nidp/saml2/metadata</saml:Issuer>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</samlp:Status>
<saml:Assertion ID="idXmEEO1dKb1ylLGE5vCZgJBYhyko"
IssueInstant="2019-12-02T17:36:29Z"
Version="2.0"
>
<saml:Issuer>https://login.customer.com/nidp/saml2/metadata</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<CanonicalizationMethod xmlns="http://www.w3.org/2000/09/xmldsig#"
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"
/>
<ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
<ds:Reference URI="#idXmEEO1dKb1ylLGE5vCZgJBYhyko">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<DigestValue xmlns="http://www.w3.org/2000/09/xmldsig#">bCDboShltlUkTx777W+omqPGFUNBGjfKNgrqN+a8RNE=</DigestValue>
</ds:Reference>
</ds:SignedInfo>
<SignatureValue xmlns="http://www.w3.org/2000/09/xmldsig#">
ygz6hfUwdzDwMvWOTj4gfIeigZYRvHMCykvncUROt7EqwUBWtvEylz6JGwP4Pv6SF/OWwuSlW7XN
tUoDIliaEPmUm9Hy3grmQnKqcNGhs9iTg9eHJPAO450iqMEMKj9DqeqVRIf3z3uYup+oKkDQv+EW
nynhAyMToudD0ZT+7DOo5Z6PbX9QIiN+IIkmcI/07A46uqsNwBIr11QSMgkM2vgFca9lKeia
iGJqodGdbhs6HAtftWoSFWJTPmqpgjKPXzawoAyaHtFlyGTSCK1PdsqzX+QPfi2WTX1xDy3rtRDx
D8wt3Mmu+AfHfm/w/OLwK0wjwn7XZe6geNbTAg==
</SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
MIIG1jCCBb6gAwIBAgIMcePUHQMz3o73XkkNMA0GCSqGSIb3DQEBCwUAMGYxCzAJBgNVBAYTAkJF
MRkwFwYDVQQKExBHbG9iYWxTaWduIG52LXNhMTwwOgYDVQQDEzNHbG9iYWxTaWduIE9yZ2FuaXph
dGlvbiBWYWxpZGF0aW9uIENBIC0gU0hBMjU2IC0gRzIwHhcNMTgxMjEzMDMzNzA0WhcNMjAxMjAz
MTcxMTAzWjB9MQswCQYDVQQGEwJDUjERMA8GA1UECBMIU2FuIEpvc2UxETAPBgNVBAcTCFNhbiBK
b3NlMSYwJAYDVQQKEx1DcmVkb21hdGljIGRlIENvc3RhIFJpY2EgUy5BLjEgMB4GA1UEAxMXbG9n
aW4uYmFjY3JlZG9tYXRpYy5jb20wggEiMA0GCSqGSIbDDDDDDQEBAQIBDwAwggEKAoIBAQDeKHRN
nMVAGLRSJ9mgJTrUY09Jd/c4Rh/7+oOAJzsCdkzrIr/LLaKOErG3Z0mY0gm5v29NneAjGs72ZXsX
gRfZ4/xa+15PNcXBZk16iRiiciNQKp+HMq4yRy0LFnS+wkUXL9cdsowm/iM9SxuOf0e6PgeOKbfo
GIluU98HWMhMXw5osuznP7oZOY0iniuEZrrlfr6b20juRGahIWR66j+WKrRno8wCLjwAF7m0Qafd
zduoupjYy1E43WEUlxUnnS7AGOnLj7G2AAAAAfy7wCTGikxXZ8FIJ2EUfcgN0iBfKZjOf37oz9ta
QuZeqi1EY9LXoUpXYKrVnHeDUnq/ER1jAgMBAAGjggNrMIIDZzAOBgNVHQ8BAf8EBAMCBaAwgaAG
CCsGAQUFBwEBBIGTMIGQME0GCCsGAQUFBzAChkFodHRwOi8vc2VjdXJlLmdsb2JhbHNpZ24uY29t
L2NhY2VydC9nc29yZ2FuaXphdGlvbnZhbHNoYTJnMnIxLmNydDA/BggrBgEFBQcwAYYzaHR0cDov
L29jc3AyLmdsb2JhbHNpZ24uY29tL2dzb3JnYW5pemF0aW9udmFsc2hhMmcyMFYGA1UdIARPME0w
QQYJKwYBBAGgMgEUMDQwMgYIKwYBBQUHAgEWJmh0dHBzOi8vd3d3Lmdsb2JhbHNpZ24uY29tL3Jl
cG9zaXRvcnkvMAgGBmeBDAECAjAJBgNVHRMEAjAAMEkGA1UdHwRCMEAwPqA8oDqGOGh0dHA6Ly9j
cmwuZ2xvYmFsc2lnbi5jb20vZ3MvZ3N131343ml6YXRpb252YWxzaGEyZzIuY3JsMCIGA1UdEQQb
MBmCF2xvZ2luLmJhY2NyZWRvbWF0aWMuY29tMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcD
AjAdBgNVHQ4EFgQUUsnCY/2dHC35dtoZ5NPp2olOie4wHwYDVR0jBBgwFoAUlt5h8b0cFilTHMDM
fTuDAEDmGnwwggF/BgorBgEEAdZ5AgQCBIIBbwSCAWsBaQB3AId1v+dZfPiMQ5lfvfNu/1aNR1Y2
/0q1YMG06v9eoIMPAAABZ6Wjq58AAAQDAEgwRgIhAIWt4+Is7SfO5e5sw3UkKSTplYP9Jlqlnh7y
SCz9Io9BAiEAu+RaBzpK1B59oJqHWjha9nFYTRAdW3FS2w+3a6aM9KcAdgCkuQmQtBhYFIe7E6LM
Z3AKPDWYBPkb37jjd80OyA3cEAAAAWelo68sAAAEAwBHMEUCIGf9tKuubZF3zfeb5clc9+A1jIeV
n+qvLmwse3OezWWtAiEApFQdfPmR6XNb1OIJzjyL+q2I6gYNoaR/VdN6EcNxcQIAdgBvU3asMfAx
GdiZAKRRFf93FRwR2QLBACkGjbIImjfZEwAAAWelo6vAAAAEAwBHMEUCIFk+RcJCv+dWTmJ1wtEq
F5EdXhqRu4mP9CHTgbASofA+AiEA78548Rd3EaS186/WCxhiU8endl3hb46QANbID5u9xw4wDQYJ
KoZIhvcNAQELBQADggEBAB8qvWlNnpx8DrjOkqsYZqCYTNh4RIXw9nR+HY6Hjiz2Enjq2cfW40Y4
U/H3RGKQAfCbrnN7lU4NZC8BwiiyonaYv4mTH0IPGGK2P1Qp9oYu/DXxAb+GR5gPeCuxYjVeNPAT
ECLr7ikPqDjMDd5IqqX2FkLAwgkb7iqtIPdv1gKcBZzRelREmrrCP+A1NM4JHQQWot2fxNVOSu4E
Xmb+DeSPuLZoxaKAYV5EE0OfBenbWkfU2AVWZkhc4wbKHisuoftKx/Z6AGXgn+By2PqUB/biRxAD
PmmyLZ8t9KkhCH/781vigjvyhOKQ10W5u1IWSjmlctLpu0kqw6FZYGAr5Uo=
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"
NameQualifier="https://login.customer.com/nidp/saml2/metadata"
SPNameQualifier="scpfiori"
>myemail@mycompany.com</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData NotOnOrAfter="2019-12-02T18:36:20Z"
Recipient="https://flpnwc-irpfpd5ihm.dispatcher.us2.hana.ondemand.com/sites/testingsite#Shell-home"
/>
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2019-12-02T17:31:29Z"
NotOnOrAfter="2019-12-02T17:41:29Z"
>
<saml:AudienceRestriction>
<saml:Audience>scpfiori</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2019-12-02T17:36:18Z"
SessionIndex="idXmEEO1dKb1ylLGE5vCZgJBYhyko"
>
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
<saml:AuthnContextDeclRef>secure/name/password/uri</saml:AuthnContextDeclRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
Name="NameID"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified"
>
<saml:AttributeValue xsi:type="xs:string">myemail@mycompany.com</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>
In the Sumarmy tab:
Issuer = https://login.customer.com/nidp/saml2/metadata
Subject = myemail@mycompany.com
NameID = myemail@mycompany.com
AttributeStatement:
* NameID = myemail@mycompany.com
The "Recipient" URL is the Fiori Launchpad configured and activated in SCP: https://flpnwc-irpfpd5ihm.dispatcher.us2.hana.ondemand.com/sites/testingsite#Shell-home
Could somebody help me to understand why am I getting this message? Am I missing something in the config?
Thanks in advance for your help.
BR.
- SAP Managed Tags:
- SAP Cloud Identity Services,
- SAP Cloud Portal service,
- SAP Business Technology Platform
Accepted Solutions (1)
Accepted Solutions (1)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Report Inappropriate Content
Hello SAP experts!
I already solved the problem that was an missconfiguration in IdP side. I'm accesing a A Fiori Launchpad on Portal Service and only as a summary in case somebody is looking for more info:
- For me was not necessary to use an attribute mapping.
- I unchecked the "Only IdP-Initiated SSO"check that is available in the trusted IdP registrarion screen.
- In productive enviroment I'm not using SAP ID Service as IdP since the configuration of both (SAP ID service and custom IdP) running at the same time (SAP ID as principal IdP and custom IdP as "Only IdP-Initiated SSO") brings some troubles.
I'm still searching for some way to configure both, SAP ID IdP and custom IdP at the same time in the Application Identity Provider. However, it looks to not be possible since SAP claims (in the official documentation) that SAP ID IdP is only for testing/exploring purposes (see official SAP documentation about Local Service Provider settings: https://help.sap.com/viewer/65de2977205c403bbc107264b8eccf4b/Cloud/en-US/dc618538d97610148155d97dcd1...)
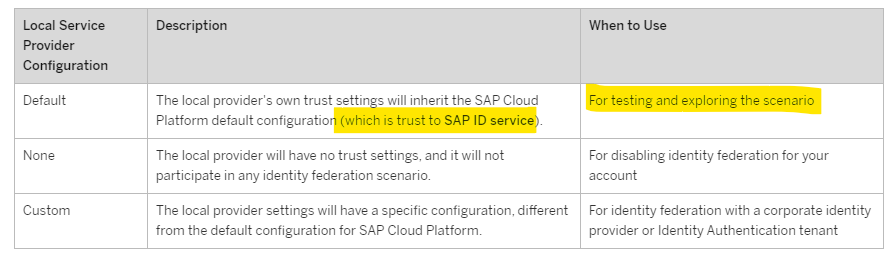
BR.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Answers (1)
Answers (1)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Report Inappropriate Content
Which service are you trying to access after setting up the IdP? The default group you assigned should have the roles relevant for the service otherwise the logged on user will not have proper authorisations and you get 401.
-Sharadha
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Report Inappropriate Content
- App to automatically configure a new ABAP Developer System in Technology Blogs by Members
- Cloud Transport Management configuration between spaces in Technology Q&A
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- What’s new in Mobile development kit client 24.4 in Technology Blogs by SAP
- Timer showing while sending the mails from SAP in Technology Q&A
| User | Count |
|---|---|
| 82 | |
| 10 | |
| 10 | |
| 9 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 3 |
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.